In the rapidly evolving digital landscape, the significance of robust security measures cannot be overstated. As cyber threats grow in sophistication, organizations must adopt advanced security frameworks to safeguard their data and systems. One such approach that is gaining traction is the adaptive security architecture design. This approach intelligently responds to threats, leveraging real-time data to adjust defenses dynamically. Through this formal examination, we explore the facets of adaptive security architecture design and its vital role in modern cybersecurity strategies.
Read Now : Effective Literature Review Strategies
The Core Principles of Adaptive Security Architecture Design
Adaptive security architecture design is grounded in several core principles that distinguish it from traditional security approaches. Primarily, it emphasizes continuous monitoring and analysis, which enables the detection of anomalies as they occur. Instead of relying solely on static defenses, adaptive security iterates its measures based on the evolving threat landscape. Another principle is its integration with artificial intelligence and machine learning, enhancing its capability to predict potential security breaches. The design also involves automated responses to certain security alerts, ensuring swift containment of threats. This proactive approach significantly reduces the window of vulnerability and potential damage.
Furthermore, adaptive security architecture design inherently supports collaboration between different security systems. By fostering communication and data sharing, it creates a holistic defense mechanism that strengthens the organizational security posture. Finally, adaptive security architecture design incorporates the vital aspect of user behavior analytics. By examining the actions and patterns of users, the architecture can identify potential insider threats and unauthorized access attempts. Together, these principles form a robust framework that promises enhanced protection against complex cyber threats.
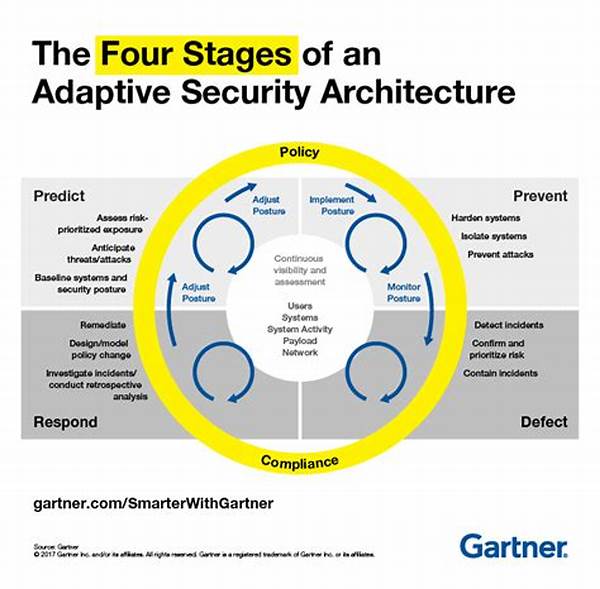
Components of Adaptive Security Architecture Design
1. Continuous Monitoring: Central to adaptive security architecture design is the constant observation of network traffic and system activities, allowing for real-time threat detection and analysis.
2. Dynamic Policy Adjustment: Policies within adaptive security architecture design are not static; they evolve based on the latest threat intelligence and assessments to remain relevant.
3. Automated Threat Response: Adaptive security architecture design incorporates automated mechanisms to respond to threats instantly, minimizing human intervention and response time.
4. Behavioral Analysis: Integral to adaptive security architecture design is the use of advanced analytics to assess user behavior patterns, identifying deviations that may indicate potential threats.
5. Intelligence Integration: By integrating threat intelligence from various sources, adaptive security architecture design enhances its predictive capabilities and fortifies defenses against emerging threats.
The Strategic Advantages of Adaptive Security Architecture Design
The implementation of adaptive security architecture design offers strategic advantages crucial for maintaining organizational cybersecurity. First, it affords heightened resilience against sophisticated cyber threats. As cybercriminals continuously refine their tactics, adaptive security ensures that defenses remain one step ahead. By incorporating real-time data and analytics, adaptive security architecture design addresses threats before they materialize into significant breaches.
Additionally, adaptive security architecture design supports regulatory compliance. With evolving data protection regulations worldwide, adaptive security architecture design assists organizations in maintaining compliance through its continuous monitoring capabilities. Furthermore, by fostering automated responses and predictive analytics, it minimizes the risk of human error, thus enhancing the overall reliability of the organization’s security framework. Overall, the strategic implementation of adaptive security architecture design not only fortifies an organization’s defenses but also aligns with long-term security and business objectives.
Implementing Adaptive Security Architecture Design
A successful implementation of adaptive security architecture design requires meticulous planning and expertise. Organizations must assess their current security posture and identify gaps that adaptive measures can fill. Moreover, the integration of existing systems with new technologies such as artificial intelligence and machine learning is paramount. The adaptive security architecture design process necessitates training for personnel to manage these sophisticated tools effectively.
1. Assessment: Gauging current security frameworks against desired adaptive capabilities.
2. Integration: Incorporating AI and ML technologies into existing security infrastructure.
3. Training: Equipping personnel with necessary skills to harness adaptive systems.
4. Testing: Rigorous testing to ensure adaptive measures function as intended.
Read Now : Premier Publications In Research Methodologies
5. Continuous Evaluation: Regular updates and evaluations to optimize adaptive system performance.
6. Stakeholder Collaboration: Engaging all organizational levels to bolster the security culture.
7. Resource Allocation: Ensuring sufficient resources are allocated for adaptive security initiatives.
8. Compliance Strategies: Aligning adaptive security initiatives with legal regulations.
9. Incident Response Plans: Establishing robust plans for immediate threat management.
10. Feedback Mechanism: Implementing feedback loops for constant improvement of adaptive systems.
Challenges and Future of Adaptive Security Architecture Design
Despite the substantial benefits, adaptive security architecture design faces several challenges. One prominent issue is the considerable investment in resources needed to deploy and sustain advanced technologies. Organizations must allocate significant budgets for infrastructure upgrades and personnel training. Furthermore, integrating adaptive security architecture design with existing legacy systems often presents technical difficulties, requiring specialized expertise.
The future of adaptive security architecture design lies in further advancements in artificial intelligence and machine learning. As these technologies evolve, adaptive security will become increasingly autonomous, effectively addressing threats with minimal human intervention. Additionally, evolving global regulatory landscapes will shape the future of adaptive security architecture design, necessitating ongoing updates to remain compliant.
Organizations must continuously evaluate and optimize their adaptive systems to remain nimble and responsive to the ever-changing threat environment. With the potential for greater automation, improved analytics, and collaborative threat intelligence, adaptive security architecture design will continue to be an indispensable element of modern cybersecurity strategies.
Adaptive Security Architecture Design and Its Role in Risk Management
Adaptive security architecture design plays an indispensable role in risk management by offering dynamic and intelligence-driven defenses. It not only identifies existing threats but also anticipates potential vulnerabilities, thereby enabling organizations to strategize proactively. By incorporating comprehensive risk assessments, adaptive security architecture design ensures that organizations are well-prepared for any eventuality.
Furthermore, this design facilitates a thorough understanding of potential risks through continuous data analysis and real-time monitoring. These capabilities allow organizations to mitigate risks efficiently and minimize impacts of possible security breaches. Ultimately, adaptive security architecture design integrates seamlessly into the broader risk management framework, bolstering organizational resilience and maintaining operational continuity in the face of potential threats.