In the modern digital ecosystem, Application Programming Interfaces (APIs) have become the backbone of seamless communication between software applications. Despite being a powerful enabler of functionality and integration, APIs also introduce a variety of security vulnerabilities that must be diligently mitigated. Ensuring secure API communication requires a well-thought-out strategy that encompasses several key principles and practices.
Read Now : **standardized Structure For Academic Papers**
Enhancing API Security through Best Practices
Implementing industry best practices is essential in reducing vulnerabilities in API communication. These practices incorporate a range of strategies focused on authentication, encryption, and monitoring. Each of these elements plays a critical role in ensuring that APIs operate securely, minimizing the risk of unauthorized access and data breaches.
Firstly, authentication is a fundamental aspect of securing API communications. It involves verifying the identity of users and applications accessing the API, typically via OAuth 2.0 or API keys. Effective authentication mechanisms significantly contribute to reducing vulnerabilities in API communication, ensuring that only authorized entities have access.
Secondly, encryption is indispensable for safeguarding data integrity and confidentiality during API exchanges. Implementing Transport Layer Security (TLS) ensures that data transmitted between clients and servers is encrypted, thus reducing vulnerabilities in API communication by protecting sensitive information from interception and tampering.
Lastly, consistent monitoring and logging of API activity are pivotal in identifying potential security threats. Establishing a robust monitoring framework helps in detecting anomalies and swiftly addressing them, thus playing an important role in reducing vulnerabilities in API communication.
Implementing Robust Authentication Measures
1. OAuth 2.0 Utilization: Employing OAuth 2.0 for authentication is essential in reducing vulnerabilities in API communication. Its access token mechanism ensures a secure, scalable, and flexible authorization process, mitigating risks associated with unauthorized data access.
2. API Key Verification: API keys serve as unique identifiers for applications, offering a basic level of access control. By utilizing API key verification, organizations can effectively control access and thereby contribute to reducing vulnerabilities in API communication.
3. Mutual TLS: Implementing mutual TLS adds an additional security layer by verifying both the client and server’s identities, thus reducing vulnerabilities in API communication and ensuring that data exchange occurs between trusted parties only.
4. Token Expiration: Implementing tokens with short expiration times ensures that any compromised tokens are of limited utility, thereby reducing vulnerabilities in API communication and enhancing overall security.
5. IP Whitelisting: Restricting API access to specific IP addresses through whitelisting limits the exposure to potential threats, thus significantly reducing vulnerabilities in API communication.
The Role of Monitoring in API Security
To effectively safeguard APIs, continuous monitoring is a crucial component. Monitoring endeavors to promptly detect and respond to suspicious activities that may indicate security breaches. In the context of reducing vulnerabilities in API communication, a systematic approach to monitoring ensures that potential threats are identified and mitigated in real-time, thereby preserving the integrity of the system.
Real-time monitoring involves tracking API requests and responses to identify any unusual patterns or anomalies. Alert systems can be set up to notify administrators of potential breaches, enabling immediate intervention. Such proactive strategies significantly contribute to reducing vulnerabilities in API communication by ensuring that security measures are consistently upheld.
Furthermore, comprehensive logging serves as an invaluable resource for forensic analysis in the aftermath of a security incident. By maintaining detailed logs of API activity, organizations can trace the origins of a breach and implement corrective measures to prevent future occurrences, thus continuously reducing vulnerabilities in API communication.
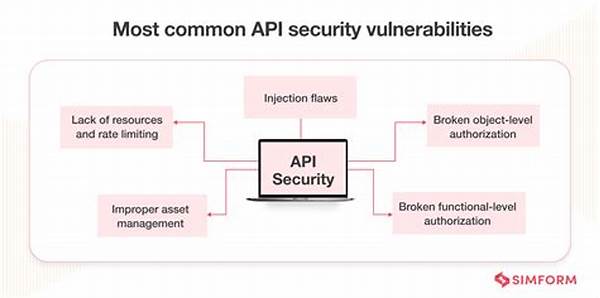
Evolving Threats and API Vulnerabilities
The landscape of digital threats is constantly evolving, presenting new challenges in reducing vulnerabilities in API communication. Cyber attackers employ sophisticated methods to exploit weaknesses in API design and implementation, emphasizing the need for vigilance and continuous improvement in security practices.
1. SQL Injection: Attackers may utilize SQL injections to manipulate an API’s database queries, gaining unauthorized access to data. Proper input validation and parameterized queries are essential in reducing vulnerabilities in API communication related to SQL injection.
2. Cross-Site Scripting (XSS): XSS attacks involve injecting malicious scripts into API responses, executing code in the end-users’ browsers. Employing content security policies reduces such vulnerabilities in API communication by restricting the execution of untrusted scripts.
3. Rate Limiting: APIs can be susceptible to abuse through excessive requests, potentially leading to denial-of-service attacks. Implementing rate limiting as a preventive measure significantly contributes to reducing vulnerabilities in API communication by controlling request volume.
Read Now : Blockchain Technology For App Security
4. Automated Testing: Regular, automated testing of the API for security weaknesses ensures timely identification and remediation, critical for reducing vulnerabilities in API communication. Testing includes simulating attacks and reviewing API responses for potential security faults.
5. Version Management: Maintaining proper version management of APIs is vital. Decommissioning outdated API versions promptly is a fundamental practice in reducing vulnerabilities in API communication, ensuring that only the most secure and up-to-date versions are in use.
6. Secure Development Practices: Throughout the API development lifecycle, employing secure coding practices is imperative. Adhering to security guidelines and conducting code reviews helps in preemptively reducing vulnerabilities in API communication.
7. Data Encryption: Encrypting data at rest and in transit is non-negotiable. Aside from TLS, using end-to-end encryption strategies is indispensable in further reducing vulnerabilities in API communication.
8. User Input Validation: Systematic validation of user inputs ensures that APIs process only legitimate data, preventing attacks that exploit user input, such as injection attacks. This is pivotal in reducing vulnerabilities in API communication.
9. Implementing Firewalls: Web Application Firewalls (WAFs) offer an additional layer of protection against malicious requests and anomalies, thereby significantly reducing vulnerabilities in API communication.
10. Security Audits: Periodic security audits by independent experts are essential in evaluating and enhancing API security postures. Such audits play a critical role in reducing vulnerabilities in API communication by identifying and addressing latent security issues.
Reducing Risks through Comprehensive API Policies
In an environment that heavily relies on interconnected services, reducing vulnerabilities in API communication is increasingly becoming a critical concern. The implementation of comprehensive and well-defined API policies is an effective strategy to mitigate potential risks. These policies serve as a blueprint guiding the secure and efficient operation of APIs, establishing guidelines for usage, security, and compliance.
First and foremost, API policies should mandate the use of encryption protocols for data transmission and storage, ensuring the protection of sensitive information from unauthorized access. By codifying these requirements, the reduction of vulnerabilities in API communication becomes systematic and consistent, laying the groundwork for a secure digital exchange.
Moreover, comprehensive API policies must outline strict access controls, specifying the conditions under which APIs can be accessed and by whom. This involves defining roles and permissions that ensure only privileged users have access to critical API functionalities, thereby reducing the possibility of data breaches and unauthorized manipulations.
The Importance of Regular Security Assessments
The evaluation of potential risks and vulnerabilities is an ongoing necessity. Regular security assessments play an integral role in reducing vulnerabilities in API communication by ensuring that security measures remain current and effective against emerging threats. Establishing a schedule for routine assessments and incorporating them into the API lifecycle is a practice that reflects an organization’s commitment to maintaining robust security protocols.
Organizations must employ both internal assessments and third-party audits to identify and rectify security weaknesses. These evaluations should include vulnerability scanning, penetration testing, and security posture analysis. By systematically addressing assessment results, enterprises effectively contribute to reducing vulnerabilities in API communication, fortifying their digital infrastructures against new and evolving threats.
Additionally, reports generated from security assessments provide insights that inform ongoing security strategies. Identifying patterns in vulnerabilities allows organizations to prioritize remediation efforts, focusing resources on the areas that most critically impact the safety and reliability of their APIs.
Conclusion
Reducing vulnerabilities in API communication is an endeavor that requires a multifaceted strategy combining technology, processes, and human oversight. The elements discussed within this article emphasize the importance of a proactive approach in securing API environments. By adhering to best practices, implementing robust security measures, and conducting regular evaluations, organizations can substantially minimize risks associated with API vulnerabilities, ultimately safeguarding data integrity and privacy.