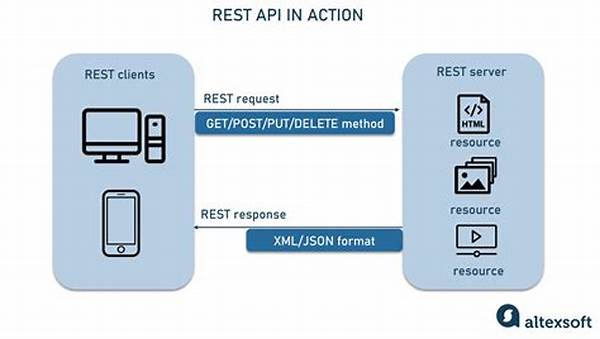
In the modern age of technological advancement, ensuring data security and privacy has become paramount. As RESTful APIs continue to proliferate as a means of efficient data exchange, the necessity for secure communication channels cannot be understated. In this regard, end-to-end encryption serves as a pivotal methodology to ensure that data remains confidential and secure throughout its journey across the network.
Read Now : Biodiversity Loss And Climate Change
The Importance of End-to-End Encryption in RESTful APIs
End-to-end encryption in RESTful APIs is a crucial component of modern digital security strategies. It ensures that data transferred between the client and server remains confidential and tamper-proof. By employing cryptographic techniques, data is encrypted at the source and only decrypted at the destination. This method ensures that intermediaries, such as Internet Service Providers (ISPs) or any nefarious actors, cannot access the data in transit. Implementing end-to-end encryption in RESTful APIs not only bolsters user trust but also complies with various regulatory standards that mandate data protection. As cyber threats become increasingly sophisticated, relying solely on traditional security measures is insufficient. Thus, adopting end-to-end encryption provides a robust layer of security, ensuring the integrity and confidentiality of data, and safeguarding sensitive information against potential breaches.
The Mechanism Behind End-to-End Encryption in RESTful APIs
1. Security Protocols: End-to-end encryption in RESTful APIs utilizes protocols like HTTPS and TLS, ensuring secure communication channels.
2. Data Integrity: It verifies that the information remains unaltered throughout the transmission process.
3. Client-Server Confidentiality: Only the communicating entities can decrypt the data, maintaining privacy.
4. Regulatory Compliance: Supports adherence to data protection regulations such as GDPR and HIPAA.
5. Trust Building: Enhances user trust by ensuring that sensitive information is protected at all stages of communication.
Implementing End-to-End Encryption in RESTful APIs
Implementing end-to-end encryption in RESTful APIs involves several critical steps to ensure secure communications. Initially, APIs must integrate protocols like HTTPS, leveraging SSL/TLS to create a secure communication channel. Further, the use of cryptographic techniques, such as public/private key encryption, plays a pivotal role in encrypting data at the client-side before it is sent to the server. This ensures that only the intended server, possessing the corresponding private key, can decrypt the data, preserving its confidentiality. Additionally, developers are encouraged to employ best practices such as rotating encryption keys regularly, using strong cryptographic algorithms, and keeping security libraries updated. As a result, these practices mitigate vulnerabilities and ensure a robust implementation of end-to-end encryption in RESTful APIs, protecting sensitive data against potential breaches and unauthorized access.
Challenges of Implementing End-to-End Encryption in RESTful APIs
1. Complexity: Implementing end-to-end encryption in RESTful APIs can be complex, requiring technical expertise.
2. Performance Impact: Encryption and decryption processes may lead to increased computational demands.
3. Key Management: Effective management of encryption keys is crucial for security.
4. Compatibility Issues: Ensuring compatibility across different platforms can be challenging.
5. Regulatory Challenges: Compliance with various regulations may require additional security measures.
Read Now : “economic Impact Of Artificial Intelligence”
6. Cost: Setting up secure encryption may incur additional costs.
7. Testing Protocols: Regular testing is necessary to uphold security standards.
8. User Perception: Users must be educated about the benefits of encryption to obtain their trust.
9. Continuous Updates: Staying ahead of security threats requires continuous updates and patches.
10. Resource Allocation: Allocating sufficient resources for encryption-related tasks is essential.
Benefits and Best Practices for End-to-End Encryption in RESTful APIs
End-to-end encryption in RESTful APIs offers numerous benefits, ensuring secure and confidential data transmission between clients and servers. This security measure not only prevents unauthorized access but also protects data integrity, ensuring that information remains unaltered during transit. Traditional methods of securing APIs, such as relying solely on server-side encryption, leave data vulnerable during transmission. Thus, end-to-end encryption becomes an imperative security strategy, enabling compliance with data protection regulations such as GDPR and HIPAA, which require stringent measures to secure personal and sensitive information.
Organizations implementing end-to-end encryption in RESTful APIs are encouraged to adhere to industry best practices to enhance their security posture. Utilizing modern encryption protocols such as TLS 1.3, regularly rotating encryption keys, and employing robust cryptographic algorithms are fundamental steps in this process. Additionally, continuous monitoring and auditing of API activities can help identify potential vulnerabilities and mitigate threats. Educating employees and stakeholders about the significance of end-to-end encryption further strengthens the organization’s overall security strategy. By adopting these practices, organizations not only ensure regulatory compliance but also build trust with their users, assuring them of the highest standards of data protection.
Strategic Planning for End-to-End Encryption in RESTful APIs
Incorporating end-to-end encryption in RESTful APIs requires strategic planning and thorough execution. This security mechanism forms an integral aspect of data protection strategies, safeguarding sensitive data during transmission. Proper planning involves evaluating the organization’s current security infrastructure and identifying areas for enhancement. By understanding the specific needs and potential threats faced by the organization, tailored encryption mechanisms can be implemented, ensuring efficient data protection against unauthorized access and cyber threats.
Regular assessment and updating of cryptographic protocols are also essential to mitigate vulnerabilities. Organizations must stay abreast of advancements in encryption technologies to incorporate the latest security features and address emerging threats effectively. Cross-departmental collaboration and investing in employee training programs further bolster the understanding and implementation of end-to-end encryption in RESTful APIs. Through strategic implementation and continuous evaluation, organizations enhance their capability to protect sensitive data, ensuring compliance with regulations and fostering trust in an increasingly interconnected digital landscape.