In an era where information transcends borders at the speed of light, the safeguarding of user data has become a cornerstone for ensuring privacy and maintaining trust. Enhanced user data protection strategies are pivotal in navigating the complexities of the digital landscape. These strategies are not merely about compliance but also about building resilient systems that protect sensitive information against an ever-evolving array of threats. As technology advances, so do the methods of those seeking to compromise data, making it imperative for companies to adopt proactive strategies that anticipate potential risks and mitigate harm effectively.
Read Now : Future Of Api Design
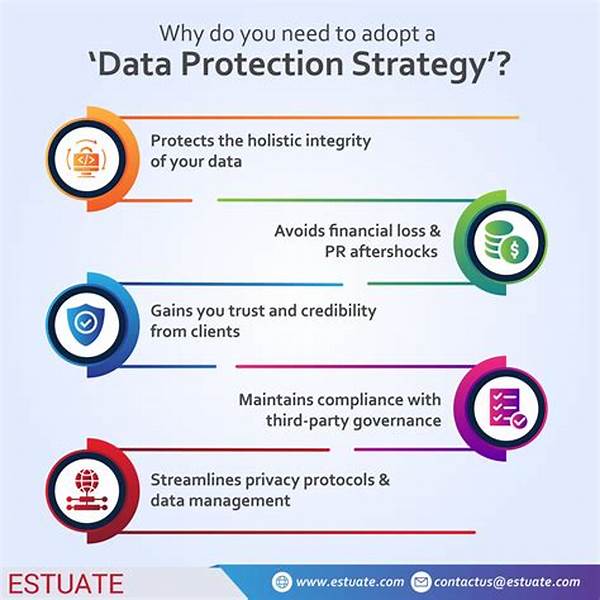
Importance of Enhanced Data Protection
Enhanced user data protection strategies are essential for maintaining the integrity and confidentiality of user information. In a digital age marked by rapid technological advancements, data breaches have become a prevalent concern, affecting millions worldwide. Businesses must prioritize robust protection mechanisms to safeguard sensitive data against unauthorized access. Implementing comprehensive encryption techniques, multi-factor authentication, and regular security audits are key components of effective data protection strategies. Organizations should foster a culture of security awareness among employees and establish stringent protocols to respond swiftly to potential breaches. Additionally, compliance with global data protection regulations ensures that companies are held accountable, promoting transparency and trust with consumers. Ultimately, these enhanced strategies not only protect the individual user’s privacy but also reinforce a company’s reputation, fostering a secure digital environment for all stakeholders involved.
Key Components of Enhanced Strategies
1. Encryption Protocols: Enhanced user data protection strategies must include robust encryption protocols to secure data at rest and in transit, ensuring unauthorized users cannot access sensitive information.
2. Access Controls: Implementing stringent access control measures is vital, allowing only authorized personnel to access critical data systems, thus mitigating the risk of internal data misuse or breaches.
3. Incident Response Plans: Formulating comprehensive incident response plans is crucial. These plans prepare organizations to react swiftly and decisively, minimizing damage in the event of a data breach or cyber attack.
4. Regular Audits: Conducting regular security audits and assessments forms an integral part of enhanced user data protection strategies, identifying vulnerabilities and reinforcing security measures where necessary.
5. Employee Training: Employee education and training programs are essential to instill awareness and understanding of security protocols, ultimately supporting the overall effectiveness of enhanced user data protection strategies.
Adapting to Technological Advances
One of the most pressing challenges in implementing enhanced user data protection strategies is staying abreast of technological advancements. As new technologies emerge, they bring with them both opportunities and risks. Companies must remain agile, continuously updating their data protection mechanisms to align with these changes. This involves not only adopting cutting-edge technologies such as blockchain and artificial intelligence for security purposes but also revisiting and revising existing strategies to ensure they are robust against contemporary threats. Enhanced user data protection strategies are not static; they demand constant evolution and adaptation to emerging trends and technologies, ensuring comprehensive protection against sophisticated cyber threats.
Simultaneously, companies must engage with industry experts to anticipate and address potential vulnerabilities that new technologies may introduce. Collaboration with cybersecurity experts, regular participation in industry forums, and adherence to best practices are vital steps in fortifying these strategies. By doing so, organizations can safeguard user data effectively, maintaining trust and confidence among their user base. Ultimately, adapting to technological advancements is a continuous process, requiring vigilance and proactive measures to uphold the highest standards of data protection and privacy.
Benefits of a Proactive Approach
Enhanced user data protection strategies that emphasize a proactive approach yield numerous advantages:
1. Minimized Risk: Proactively identifying vulnerabilities reduces the likelihood of data breaches, thereby protecting sensitive user information effectively.
2. Reputation Management: Companies that implement comprehensive strategies enhance their reputations, fostering trust among their clientele and gaining a competitive advantage in the marketplace.
3. Regulatory Compliance: Staying ahead of compliance issues through proactive strategies safeguards organizations from potential legal and financial repercussions associated with data breaches.
4. Customer Trust: Enhanced user data protection strategies build customer loyalty by providing assurance that personal information is treated with the utmost care and security.
Read Now : Big Data Integration Strategies
5. Cost Efficiency: Investing in preventative measures reduces long-term costs associated with breach remediation, legal fees, and damage control initiatives.
6. Innovation Encouragement: Proactive data protection encourages innovation by providing a secure environment for the development and deployment of new technologies and services.
7. Threat Mitigation: Timely identification and neutralization of potential threats before they materialize into significant incidents protect organizational integrity.
8. Business Continuity: Ensuring data availability and integrity contributes to seamless business operations, maintaining continuity even amidst potential security challenges.
9. Data Integrity: Enhanced user data protection strategies ensure the accuracy and reliability of data, critical for informed decision-making processes within organizations.
10. Global Market Access: Compliance with international data protection standards opens avenues to global markets, expanding business opportunities without compromising user data security.
Addressing Privacy Concerns
Addressing privacy concerns is an integral aspect of enhanced user data protection strategies. With the growth of digital platforms, users have become increasingly concerned about how their personal data is used, stored, and shared. Organizations must, therefore, prioritize transparency in their data handling practices. Clear communication about data collection methods, the purpose for data usage, and the duration for which data is retained, can alleviate privacy concerns and foster user confidence. Regular updates and user-friendly privacy policies ensure that users are well-informed about how their data is protected.
Moreover, offering users greater control over their personal information, such as easy options to opt-out of data collection or to access and modify their data, reinforces trust and user empowerment. Incorporating privacy by design into the development of new products and services also demonstrates a commitment to protecting user privacy from the outset. Enhanced user data protection strategies that prioritize privacy not only comply with stringent regulations but also differentiate a company as a responsible steward of user information.
Elevating Standards of Protection
Elevating the standards of user data protection involves a multi-faceted approach. Firstly, a robust legal framework is essential, ensuring compliance with international and local regulations such as the General Data Protection Regulation (GDPR) or the California Consumer Privacy Act (CCPA). These frameworks provide a blueprint for organizations to follow, establishing a baseline for data protection practices that should be met or exceeded.
Additionally, the integration of state-of-the-art technology is paramount. Utilizing advanced analytics, artificial intelligence, and machine learning can help in early detection of potential threats. Moreover, investing in talent acquisition by hiring skilled cybersecurity professionals ensures that organizations are ready to address complex security challenges. Finally, continuous improvement through regular reviews of security policies and updating protocols to address evolving threats is crucial. By proactively enhancing these standards, organizations can effectively protect user data and maintain their reputation as trustworthy entities committed to safeguarding privacy.
Strategic Summary and Future Directions
In conclusion, the significance of enhanced user data protection strategies cannot be overstated in today’s digital age. These strategies encompass a range of practices designed to anticipate and mitigate threats, ensuring sensitive user information remains safeguarded. The future of data protection lies in a harmonious blend of rigorous security measures, robust technological solutions, and a dedicated commitment to user privacy. As the landscape of cyber threats continues to evolve, organizations must remain steadfast in their efforts to protect user data and uphold the integrity of their operations. The journey toward enhanced user data protection is ongoing, characterized by innovation, vigilance, and a resolute dedication to privacy. Through these efforts, organizations can foster a secure digital environment that not only meets regulatory demands but exceeds user expectations, setting a benchmark for future data protection endeavors.