Securing RESTful API endpoints is of paramount importance in today’s digital landscape, where APIs serve as the backbone for numerous applications and data exchanges. In the absence of robust security measures, API endpoints can become vulnerable targets for malicious attacks, data theft, and unauthorized access. This article endeavors to explore the critical methodologies and practices associated with the process of securing RESTful API endpoints, emphasizing the importance of protecting sensitive information and ensuring the integrity of communication between clients and servers.
Read Now : Improving Support Infrastructure Modernization
Importance of API Security
The importance of securing RESTful API endpoints cannot be overstated, as the proliferation of API integrations across industries increases the likelihood of unauthorized access and data breaches. API endpoints serve as channels through which data is exchanged between different software systems, making them prime targets for cybercriminals. Implementing security measures such as authentication, authorization, and encryption ensures that only legitimate users can access the API endpoint, thereby safeguarding sensitive data from malicious actors.
In addition, securing RESTful API endpoints involves establishing comprehensive monitoring and auditing mechanisms to detect and respond to suspicious activities. These mechanisms aid in identifying potential security vulnerabilities and ensuring compliance with data protection regulations. By monitoring API traffic and user activities, organizations can proactively address security concerns, maintain data confidentiality, and reinforce trust with users.
The ongoing evolution of security threats necessitates continuous updates and improvements in API security practices. Organizations must stay informed about emerging threats and adopt advanced security technologies to protect their API endpoints. Securing RESTful API endpoints ultimately contributes to the overall security posture of an organization, ensuring seamless and secure interactions in an increasingly interconnected digital world.
Methods to Secure API Endpoints
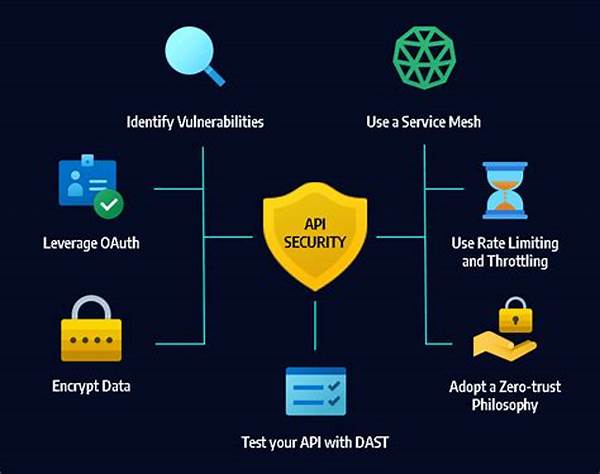
1. Authentication Mechanisms: Implementing strong authentication mechanisms is crucial for securing RESTful API endpoints. This ensures that only authorized users can access the API, thereby preventing unauthorized access.
2. Encryption of Data: Encrypting data in transit and at rest is vital for securing RESTful API endpoints. This practice shields sensitive information from interception and unauthorized access.
3. Rate Limiting: Applying rate limiting techniques helps in securing RESTful API endpoints by deterring malicious users from performing excessive requests that can lead to denial-of-service attacks.
4. Input Validation: Regular input validation is necessary to secure RESTful API endpoints. By validating user inputs, organizations can prevent injection attacks and ensure data integrity.
5. Audit and Monitoring: Establishing comprehensive audit and monitoring systems is essential for securing RESTful API endpoints. These systems detect anomalies and facilitate timely responses to potential threats.
Challenges in API Security
Securing RESTful API endpoints encompasses numerous challenges that organizations must address in order to maintain robust security. A primary challenge is the requirement for seamless integration of security measures without hindering the functionality or performance of the API. Developers must balance security implementations with user experience to ensure efficient data transmission while safeguarding sensitive information from unauthorized access and cyber threats.
Another significant challenge in securing RESTful API endpoints lies in managing access controls effectively. Implementing stringent access control policies is crucial to ensure that only authorized users have access to specific resources. This entails defining user roles and permissions meticulously, as well as continually updating and reviewing these policies to adapt to changing security landscapes. By addressing these challenges, organizations can fortify their API security strategies and protect their digital assets from potential exploits and vulnerabilities.
Implementing Security Best Practices
Practical Steps for Enhanced Security
When it comes to securing RESTful API endpoints, employing security best practices is essential for safeguarding sensitive information and ensuring the reliability of API interactions. Below are ten explanations of critical security measures:
1. API Key Management: Secure storage and management of API keys prevent unauthorized users from accessing sensitive endpoints.
2. TLS/SSL Encryption: Ensuring encrypted communication between clients and servers shields data from interception during transmission.
3. IP Whitelisting: Restricting access to API endpoints by allowing only trusted IP addresses to connect enhances security.
Read Now : Restful Architecture Scalability Benefits
4. CORS Policies: Defining Cross-Origin Resource Sharing policies mitigates risks associated with cross-origin requests.
5. OAuth2 Implementation: Utilizing OAuth2 protocols ensures secure user authentication and authorization for accessing API resources.
6. Security Patches: Regularly updating API components with security patches prevents exploitation of known vulnerabilities.
7. Incident Response Plan: Developing a comprehensive incident response plan prepares organizations for timely reactions to security breaches.
8. Access Logs: Maintaining detailed access logs provides insights into user interactions and assists in identifying unusual activities.
9. API Gateway Utilization: Utilizing an API gateway provides centralized control and management of API traffic, enhancing security features.
10. Token-Based Authentication: Implementing token-based authentication strengthens security by offering temporary credentials for accessing APIs.
The Future of API Security
As the technological landscape continues to evolve, the future of securing RESTful API endpoints will be shaped by advancements in security protocols and emerging threats. Organizations will increasingly leverage artificial intelligence and machine learning technologies to enhance threat detection and automate responses, thereby strengthening their API security posture. By employing predictive analytics and anomaly detection, businesses can identify potential vulnerabilities proactively and devise strategies to mitigate them.
Furthermore, securing RESTful API endpoints will require organizations to adopt a holistic approach to security, integrating API protection within broader cybersecurity frameworks. Continuous education and training for developers and security teams will be paramount to staying ahead of evolving threats and ensuring compliance with industry standards and regulations. In a world where digital transformation accelerates, securing RESTful API endpoints will remain a crucial aspect of protecting valuable data assets and maintaining the trust of stakeholders.
Conclusion
Final Thoughts on API Security
In conclusion, securing RESTful API endpoints is a fundamental aspect of modern software development and integration, essential for protecting sensitive information and ensuring the fidelity of data exchanges. The dynamic nature of cybersecurity threats necessitates a proactive approach to secure API endpoints, encompassing robust authentication, encryption, and monitoring measures. Organizations must remain vigilant in addressing the security challenges posed by evolving technologies and persistent cyber threats, constantly updating their security protocols and practices.
Moreover, fostering a culture of security awareness within organizations is vital for the successful implementation and maintenance of API security strategies. Training and educating developers, as well as establishing comprehensive security policies and guidelines, will build a resilient security framework and safeguard digital ecosystems from potential exploits. Through concerted efforts and adoption of best practices, securing RESTful API endpoints will continue to be a cornerstone of robust cybersecurity in an increasingly interconnected digital environment.