Understanding Blockchain-Based Authentication for Apps
In an era where digital transformation governs the business landscape, the prominence of secure authentication mechanisms is pivotal. Blockchain-based authentication for apps is emerging as a game-changing technology in enhancing security protocols. Decentralized and tamper-proof, blockchain technology ensures that authentication processes are more robust than traditional systems. Unlike conventional methods relying on centralized servers, this decentralized approach diminishes the single point of failure, thereby enhancing security by distributing authentication data across multiple nodes.
Read Now : Weather Data For Farm Decision Making
Moreover, blockchain-based authentication for apps establishes an immutable record of user activities. The transparency and traceability that blockchain offers can significantly alleviate issues such as unauthorized access and data tampering. By ensuring that each transaction is cryptographically secured and logged in the distributed ledger, this technology provides an auditable trail that uplifts transparency. Consequently, sectors including finance, healthcare, and supply chain are increasingly deploying blockchain-based solutions to secure their applications and user data.
Furthermore, blockchain-based authentication for apps fosters user trust. Users are more inclined to engage with digital platforms when they are assured that their data privacy is upheld. Blockchain’s decentralized nature ensures data integrity and enhances user privacy by avoiding the need to hold personal information on centralized servers. Thus, leveraging blockchain-based authentication not only fortifies security but also builds a foundation of trust between service providers and their user base.
The Advantages of Blockchain-Based Authentication
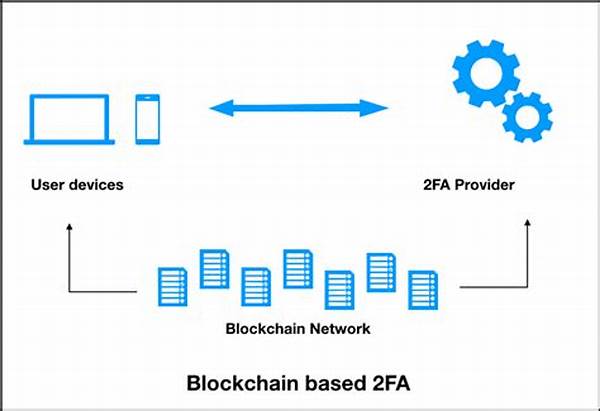
Blockchain-based authentication for apps eliminates reliance on centralized servers by distributing data across a secure, decentralized network. This distribution prevents single points of failure, enhancing security and system resilience.
The transparency of blockchain technology facilitates immutable record-keeping. Each authentication event is logged on the blockchain, providing an auditable and traceable trail of user actions.
Blockchain-based authentication for apps enhances data security through cryptographic techniques. By encrypting user data and distributing it across a decentralized network, blockchain ensures data integrity and prevents unauthorized access.
This form of authentication ushers in enhanced user privacy. Blockchain’s decentralized structure obviates the need for storing personal information, safeguarding user confidentiality.
Adopting blockchain-based authentication promotes trust in digital platforms. Users feel more secure knowing their engagements are protected by a robust, immutable system, strengthening user confidence and engagement.
Implementing Blockchain-Based Authentication in App Development
The implementation of blockchain-based authentication for apps requires a multifaceted approach that integrates technological innovation with strategic planning. Initial steps involve architecting a decentralized system that leverages blockchain protocols tailored to authentication processes. This entails selecting a suitable blockchain framework that aligns with the application’s security requirements. Considerations regarding scalability, compatibility, and transaction throughput play a critical role in shaping the foundational architecture of the authentication system.
Once the infrastructure is established, the next phase involves developing robust cryptographic mechanisms to ensure secure user authentication and data protection. Implementing smart contracts can automate the processes of user verification, minimizing the potential for human error and malicious interference. Smart contracts allow predefined conditions to be fulfilled automatically, ensuring seamless and secure authentication processes that are both efficient and immutable.
The integration of blockchain-based authentication for apps also necessitates comprehensive testing and validation to identify potential vulnerabilities and ensure system robustness. Simulation of diverse user scenarios under varied conditions is essential to ascertain the application’s resilience and ability to withstand attacks. Furthermore, continuous monitoring and periodic audits are imperative to maintain the integrity and performance of the authentication system, ensuring that it remains impervious to emerging threats and aligns with evolving cybersecurity norms.
Key Considerations for Blockchain-Based Authentication Deployment
1. System architecture must accommodate decentralized network dynamics, focusing on scalability and interoperability.
2. Selection of blockchain protocols should align with the specific security and operational needs of the app.
3. Implementation of cryptographic algorithms is crucial to safeguarding user data and ensuring privacy.
4. Smart contracts should be employed for automating secure authentication processes.
Read Now : Implementing Tls For Api Security
5. Ensuring system resilience through rigorous testing under varying conditions is vital.
6. Continuous monitoring protocols are essential to identify and neutralize emerging threats.
7. Compliance with evolving cybersecurity standards must be maintained.
8. User experience should remain seamless and unaffected by underlying complex encryption processes.
9. Performance metrics need regular evaluation to ensure alignment with desired authentication outcomes.
10. Stakeholder engagement in the deployment process can aid in the adoption and optimization of the system.
Challenges in Implementing Blockchain-Based Authentication
Implementing blockchain-based authentication for apps is not without its challenges. One primary concern is scalability. Blockchain networks can face throughput limitations, particularly in public blockchains where transaction speeds can impact the user experience. Developers are tasked with balancing the security benefits of blockchain with the need for a responsive and efficient authentication process.
Another significant challenge is the complexity of the technology. Blockchain is inherently intricate, and integrating it into existing IT infrastructures requires specialized skills and knowledge. Organizations must invest in training and development or collaborate with experts who possess the requisite blockchain expertise. Additionally, the cost implications of implementing such a system can be substantial, necessitating careful budgeting and resource allocation.
Legal and regulatory considerations also play a crucial role. The decentralized nature of blockchain can present compliance challenges, especially in jurisdictions with stringent data protection laws. Ensuring that blockchain-based authentication for apps adheres to regulatory frameworks requires a thorough understanding of evolving legal standards and the dynamic digital landscape. Balancing innovation and compliance necessitates vigilance and adaptability in navigating these regulatory demands.
Enhancing User Trust through Blockchain-Based Authentication
Building User Confidence with Blockchain-Based Authentication
Blockchain-based authentication for apps has the potential to significantly enhance user trust. The technology’s inherent transparency and security features allow users to interact with applications with greater assurance of data protection. Knowing that their personal information is distributed across a decentralized network rather than stored centrally empowers users by reducing the risk of data breaches and unauthorized access.
Transparency plays a pivotal role in fostering trust. Blockchain-based authentication implements an open, verifiable ledger that users can audit, ensuring that every authentication event is genuine and untampered. This transparency extends beyond data security, as it also provides users with insights into how their data is being utilized. Such visibility is instrumental in building a trustworthy relationship between service providers and users.
Moreover, blockchain-based authentication for apps enhances user autonomy. With the elimination of third-party intermediaries who traditionally control access to user data, individuals gain greater control over their digital identities. Empowering users in this manner nurtures a sense of ownership and trust, reinforcing their confidence in engaging with digital platforms secured by blockchain technology.