In the contemporary digital era, the necessity to safeguard information cannot be underestimated. Organizations, both large and small, face the daunting challenge of securing their data against unauthorized access and cyber threats. Implementing robust authentication techniques is crucial to ensuring that users are who they say they are, thereby mitigating security breaches and enhancing trust in digital interactions. This article delves into the strategies and significance of instituting such security measures, providing a comprehensive overview for organizations keen on strengthening their authentication frameworks.
Read Now : Interdisciplinary Research Collaborations
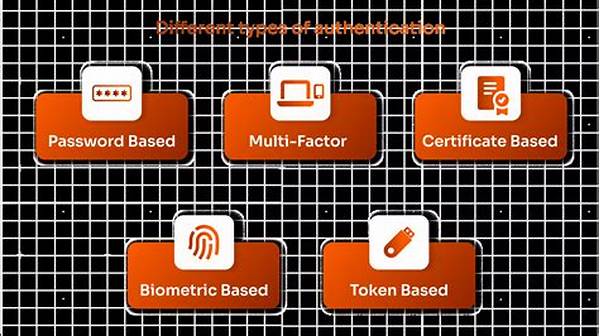
Importance of Robust Authentication
The significance of implementing robust authentication techniques lies in their capacity to protect sensitive data and user identities. With the proliferation of digital platforms, the reliance on passwords alone has proven inadequate. Multi-factor authentication (MFA), biometric recognition, and other advanced mechanisms offer layers of protection that are difficult to compromise. Such techniques serve as the backbone of a secure digital environment, reducing vulnerabilities that malicious actors might exploit.
Organizations dedicated to safeguarding their information assets must acknowledge the increasing sophistication of cyber threats. Implementing robust authentication techniques involves adopting an approach that incorporates the latest technologies and addresses potential threats comprehensively. With cyberattacks becoming more advanced, it is imperative to consult existing literature and case studies highlighting the successful adoption of strong authentication methods.
Furthermore, implementing robust authentication strategies not only enhances security but also builds user confidence. Customers become more inclined to engage with platforms that guarantee the protection of their personal data. As a consequence, businesses experience heightened customer loyalty and engagement, driving their overall growth and success in the competitive market landscape.
Strategies for Implementing Robust Authentication
1. Emphasizing the integration of biometrics is essential in the quest for improved security. Implementing robust authentication techniques with fingerprint, facial recognition, and iris scans reduces the burden of remembering complex passwords.
2. Adaptive authentication adjusts security measures based on user behavior, location, or device. This method is critical when implementing robust authentication techniques, as it dynamically adjusts protections without user interference.
3. Utilizing hardware tokens or smart cards is a proven approach for implementing robust authentication techniques, providing tangible evidence of a user’s identity that further secures digital interactions.
4. One-time passwords (OTPs) offer an additional layer of security. By implementing robust authentication techniques that use time-sensitive OTPs, organizations can thwart unauthorized access effectively.
5. Risk-based authentication evaluates the context of a user’s login attempt. Implementing robust authentication techniques in this manner ensures a proactive response to unusual activities, enhancing overall security posture.
Challenges in Authentication Implementation
Implementing robust authentication techniques is not without challenges. Organizations often encounter obstacles such as cost, complexity, and user resistance. These issues necessitate careful planning and execution to ensure that new measures do not hinder user experience or operational efficiency. It is crucial to strike a balance between stringent security protocols and seamless access for legitimate users.
Moreover, implementing robust authentication techniques requires the integration of new technologies into existing systems. This may involve substantial investment and time to train staff, update infrastructure, and manage transition phases. Organizations must also consider the potential impact on system performance and be prepared to optimize processes accordingly to maintain a high standard of service.
Successfully implementing robust authentication techniques often necessitates collaboration across departments and with external experts. By engaging in comprehensive planning and consistently evaluating the system’s effectiveness, organizations can overcome these challenges and achieve a higher level of security assurance.
Benefits of Enhanced Authentication
1. Implementing robust authentication techniques strengthens data security by making it harder for unauthorized users to gain access.
2. Enhanced authentication fosters customer trust, encouraging them to engage more with the platform.
3. With robust techniques in place, organizations experience reduced incidences of data breaches, safeguarding their reputation.
4. Regulatory compliance is more manageable when implementing robust authentication techniques, helping avoid potential fines.
5. Organizations that invest in robust authentication can distinguish themselves as security-conscious leaders in their industry.
Read Now : Implementing Scalable Big Data Solutions
6. Implementing robust authentication techniques aids in tracking user access, providing invaluable audit trails.
7. Strong authentication protocols offer scalability, accommodating growing user bases without compromising security.
8. Implementing robust authentication techniques allows the adoption of cutting-edge technology, staying ahead of threats.
9. Organizations can reduce fraud by implementing robust authentication techniques, thus saving on potential financial losses.
10. Enhanced security protocols often lead to operational efficiencies, streamlining user access management and reducing administrative burdens.
Case Study: A Comprehensive Approach
When implementing robust authentication techniques, one key case study involves a multinational financial institution revamping its security systems. Facing persistent cyber threats, the institution prioritized robust authentication by introducing multi-factor authentication (MFA) across its user base. They implemented solutions that combined biometric verification with hardware tokens to ensure an additional layer of security.
The initial phase involved assessing the existing infrastructure to determine the compatibility of new authentication measures. The institution conducted extensive user testing to ensure the methodologies were both secure and user-friendly, minimizing disruption. By implementing robust authentication techniques, they were able to significantly reduce unauthorized access attempts and bolster customer confidence in their security measures.
Additionally, the company undertook a robust communication strategy to educate customers and employees about the new measures. This included detailed instructions on how to navigate the new systems and the reasons behind these changes. By implementing robust authentication techniques effectively, the institution not only enhanced security but also improved customer satisfaction and trust, leading to an increase in their market share.
Implementing Authentication in Cloud Services
The integration of cloud services into business operations has skyrocketed in recent years. Implementing robust authentication techniques in this realm is crucial for maintaining data integrity and security. Cloud environments, by their nature, present unique challenges given their increased exposure to the internet and the shared security model between providers and users.
When implementing robust authentication techniques for cloud services, it is important to understand the division of responsibilities. Cloud service providers typically offer a baseline level of security, but it falls upon the organization to implement additional measures to protect sensitive data and applications. This often involves utilizing identity and access management (IAM) solutions that support multi-factor authentication, robust logging, and real-time monitoring to detect and thwart unauthorized access attempts.
Organizations must also consider regulatory requirements unique to their industry, ensuring compliance with standards such as GDPR, HIPAA, or others that dictate how data should be protected in cloud environments. Implementing robust authentication techniques that align with these regulatory frameworks not only ensures compliance but also builds trust with customers who are increasingly concerned about how their data is handled and protected.
Concluding Summary
In conclusion, the importance of implementing robust authentication techniques cannot be overstated in today’s digital age. These techniques form the cornerstone of secure operations across industries, protecting both organizations and their customers from the detrimental effects of data breaches. Through careful planning, strategic investment, and ongoing evaluation, companies can successfully implement these techniques to enhance their security posture.
As cyber threats continue to evolve, adopting a proactive stance by implementing robust authentication techniques is not just advisable; it is essential. This commitment to security translates into tangible benefits, including protecting valuable data, ensuring regulatory compliance, and maintaining the trust and loyalty of customers. Organizations that prioritize and invest in robust authentication are well-positioned to navigate the complex landscape of modern digital security, safeguarding their operations and paving the way for sustained success.