In the rapidly evolving landscape of digital technology, ensuring data security and privacy has never been more paramount. As the digital world continues to expand, so does the complexity and sophistication of threats targeting sensitive information. Consequently, technological advancements such as blockchain-based encryption methodologies have emerged as imperative solutions, offering robust protection against unauthorized access and breaches. This article delves into the intricacies and significance of these methodologies, exploring their key components and advantages in safeguarding digital assets.
Read Now : Weather Fluctuations In Agricultural Cycles
The Foundations of Blockchain-Based Encryption Methodologies
Blockchain-based encryption methodologies utilize the core principles of blockchain technology to enhance data security. At the heart of this approach lies a decentralized ledger, which ensures that transactions are securely recorded across multiple nodes. This decentralization is pivotal in minimizing the risks of a single point of failure, making unauthorized data access remarkably difficult. Furthermore, the cryptographic techniques employed serve to encrypt data within each block, preserving its integrity and confidentiality.
The implementation of blockchain-based encryption methodologies involves intricate cryptographic algorithms designed to secure data exchanges between parties. These methodologies capitalize on the unparalleled transparency, traceability, and security of blockchain networks, thus fostering trust among users. With every transaction verified and encrypted, the data remains immutable and tamper-proof. As a result, organizations can safely engage in data sharing and transactions without fearing potential integrity breaches, thus significantly enhancing business operations and customer trust.
Moreover, blockchain-based encryption methodologies are increasingly being recognized for their potential to revolutionize various industries. From finance to healthcare, these technologies can securely conduct transactions, manage records, and verify identities without exposing critical data to cyber threats. Given their robustness and adaptability, blockchain-based encryption methodologies are poised to redefine data security paradigms, offering an innovative approach to counteract the relentless advancements of cyber adversaries.
Key Features of Blockchain-Based Encryption Methodologies
1. Decentralization: Blockchain-based encryption methodologies eliminate the reliance on a central authority, distributing data across multiple nodes to enhance security.
2. Immutability: Data entered into the blockchain is irreversible, ensuring permanent and unalterable records which are crucial for data integrity.
3. Transparency: The transparent nature of blockchain technology allows all parties involved to access transaction records, fostering trust and accountability.
4. Cryptographic Security: Strong cryptographic algorithms form the backbone of blockchain-based encryption methodologies, safeguarding data against unauthorized access.
5. Smart Contracts: These methodologies enable automated transaction validation through smart contracts, facilitating secure and efficient business operations.
Benefits of Blockchain-Based Encryption Methodologies
Blockchain-based encryption methodologies offer substantial benefits in the realm of data security. By leveraging the decentralized nature of blockchain technology, organizations can ensure that their data storage and transmission systems are robust and resilient against attacks. This decentralized framework eliminates the vulnerability associated with centralized systems, reducing the risk of data breaches and unauthorized access. Hence, stakeholders can confidently engage in transactions that demand high levels of privacy and security.
Moreover, these methodologies enhance data integrity by ensuring that any alterations to the data are evident and traceable. This feature is particularly valuable in industries where data accuracy is paramount, such as finance and healthcare. By employing blockchain-based encryption methodologies, organizations can maintain comprehensive records of transactions and exchanges, thereby bolstering their capability to audit and verify data. This ensures transparency and compliance with regulatory standards, which are increasingly vital in the digital age.
In addition, blockchain-based encryption methodologies provide scalability and flexibility, enabling organizations to adapt to evolving data security needs. As cyber threats become more sophisticated, the ability to modify encryption protocols without compromising stored data is of utmost importance. The inherent structure of blockchain technology allows for such adaptability, ensuring long-term data protection and security in a rapidly changing technological landscape.
Read Now : Principles Of Api Standardization
Challenges of Implementing Blockchain-Based Encryption Methodologies
Numerous challenges accompany the implementation of blockchain-based encryption methodologies. First, the complexity of these systems demands significant technological expertise and resources. Organizations must invest in training and infrastructure to effectively deploy these methodologies, which can entail substantial costs. Additionally, integrating blockchain systems with existing IT infrastructure poses compatibility challenges, often requiring extensive modifications to current systems and processes.
Furthermore, the energy consumption associated with blockchain technologies is a concern that organizations must address. The process of validating transactions within a blockchain involves resource-intensive computations, leading to significant energy usage. This has prompted endeavors to develop more energy-efficient alternatives without compromising security. Lastly, regulatory hurdles complicate the adoption of blockchain-based encryption methodologies, as jurisdictions grapple with creating frameworks that accommodate the unique features of blockchain technology.
The Future Prospects of Blockchain-Based Encryption Methodologies
The trajectory of blockchain-based encryption methodologies is promising, with potential expansions into various domains. With advancements in quantum computing on the horizon, traditional encryption methods risk obsolescence, heightening the need for innovative solutions like blockchain. The ability to seamlessly integrate blockchain-based encryption methodologies with emerging technologies will be critical in maintaining secure digital environments. Industries stand to benefit from collaborative efforts that harness the strengths of blockchain, addressing global challenges in data security and privacy.
As blockchain technology matures, increased regulatory clarity is likely to spur adoption, facilitating new applications and innovations. Enhanced collaboration between industry stakeholders and regulatory bodies will be instrumental in navigating the complexities of blockchain-based encryption, ensuring that these methodologies continue to evolve alongside technological advancements. Consequently, organizations must remain vigilant and proactive in integrating these technologies into their operations to capitalize on the full potential of blockchain-based encryption methodologies.
Intricacies of Blockchain-Based Encryption Mechanisms
In understanding blockchain-based encryption methodologies, it is essential to dissect their underlying mechanisms. Primarily, the foundation of these methodologies lies in consensus algorithms, which validate and record transactions uniformly across all nodes. This reduces the risk of fraudulent activity, as consensus among nodes is required for data entry. Additionally, hashing techniques ensure data consistency and integrity, as each block’s hash is a function of its contents. Altering the data within a block changes its hash, signaling tampering attempts.
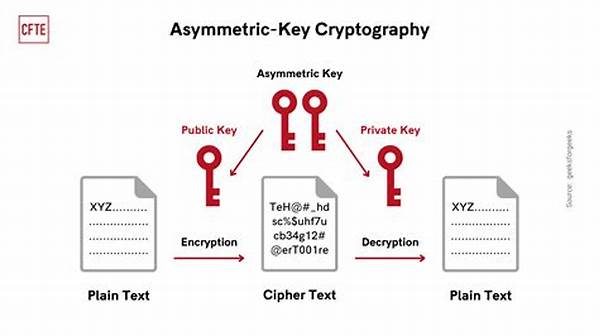
The deployment of private and public keys is another intricate aspect of blockchain-based encryption methodologies. Public keys serve as addresses within the network, while private keys grant permission to access or modify data. This dual-key system operates as a security measure, preventing unauthorized data access. Moreover, the implementation of digital signatures confirms the authenticity of data exchanges, contributing to the reliability and trustworthiness of blockchain networks.
Summary of Blockchain-Based Encryption Methodologies
Blockchain-based encryption methodologies represent a significant stride towards ensuring data security in an era where digital information is both widespread and vulnerable. The decentralized architecture of blockchain enhances the resilience of data systems against unauthorized alterations, bolstering trust between transacting parties. Organizations adopting these methodologies can leverage enhanced data integrity, transparency, and traceability, all of which are fundamental to complying with stringent regulatory standards that govern data management practices.
One of the significant virtues of blockchain-based encryption methodologies is their adaptability to an organization’s evolving needs. As the complexity and frequency of cyber threats increase, the ability to refine and upgrade encryption protocols becomes critical. The structural malleability inherent in blockchain technology supports this dynamic adjustment, enabling sustained protection of valuable data assets. Consequently, organizations can safeguard sensitive information against both present and emerging threats, preserving data confidentiality and integrity.