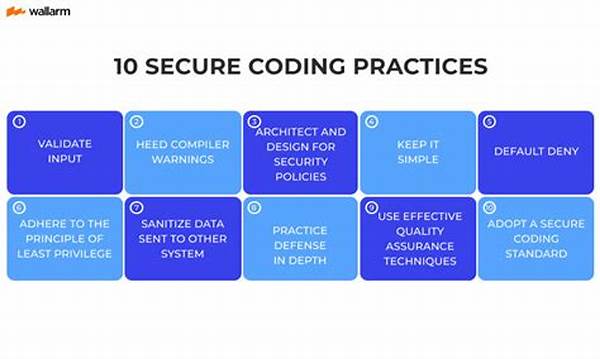
In the ever-evolving landscape of software development, the importance of secure coding practices cannot be overstated. As cyber threats continue to grow in sophistication and frequency, developers are tasked with not only creating functional and efficient software but also ensuring that their code is resilient against security vulnerabilities. Secure coding practices are essential in safeguarding sensitive information, maintaining user trust, and protecting the integrity of applications.
Read Now : Crop Yield And Climate Change
Understanding the Importance of Secure Coding Practices
The significance of best practices for secure coding lies in their ability to mitigate potential security threats that software applications face daily. By adhering to these practices, developers can avoid common vulnerabilities such as buffer overflows, injection attacks, and unauthorized data access. Security breaches can result in substantial financial losses, damage to reputation, and loss of user trust. Therefore, incorporating secure coding practices from the inception of a project is paramount. These practices involve a comprehensive understanding of potential vulnerabilities, continuous education on emerging threats, and the implementation of robust coding standards. Additionally, utilizing automated tools to scan code for vulnerabilities and conducting regular code reviews can significantly reduce the occurrence of security issues. Secure coding is not a one-time effort but an ongoing commitment to excellence and vigilance in the software development lifecycle. By prioritizing secure coding practices, organizations can build resilient applications that stand the test of time.
Essential Guidelines for Secure Coding
1. Regular code reviews are fundamental to best practices for secure coding, as they provide opportunities for identifying and addressing vulnerabilities early in the development process.
2. Implementing least privilege principles restricts user access rights to the bare minimum necessary, enhancing security through best practices for secure coding.
3. Using prepared statements in database interactions prevents SQL injection attacks, a crucial aspect of best practices for secure coding.
4. Input validation is a core component of best practices for secure coding, ensuring that application inputs are thoroughly checked against expected formats and values.
5. Continuous security training for developers is vital to keeping up with evolving threats and solidifying best practices for secure coding.
Integrating Secure Coding into Development Pipelines
Incorporating best practices for secure coding into the development process requires a strategic approach that aligns with organizational objectives. It begins with establishing a security-focused culture that prioritizes security at every stage of development. By integrating security protocols directly into the continuous integration and continuous deployment (CI/CD) pipeline, organizations can automate security checks and ensure that each code iteration complies with established security standards. This proactive approach minimizes the risk of vulnerabilities being introduced into the codebase. Best practices for secure coding also involve leveraging penetration testing and threat modeling to anticipate and defend against potential attacks. By simulating real-world attack scenarios, developers can identify weaknesses and adjust their strategies accordingly. Furthermore, fostering collaboration between development and security teams ensures that security considerations are ingrained in the development process, ultimately resulting in secure, reliable, and resilient software solutions.
Techniques for Implementing Secure Coding
1. Conduct threat assessments regularly to identify potential security risks is key to best practices for secure coding.
2. Establish a coding standard that emphasizes security and is aligned with industry benchmarks.
3. Utilize automatic code analysis tools to detect potential security vulnerabilities early.
4. Encrypt sensitive data both in transit and at rest to prevent unauthorized access.
Read Now : Ai-enhanced Financial Forecasting Models
5. Ensure robust error handling to avoid disclosing sensitive information inadvertently.
6. Monitor third-party libraries for known vulnerabilities to maintain best practices for secure coding.
7. Use a multifactor authentication system to bolster access security.
8. Apply strict patch management procedures to ensure systems are up-to-date with security fixes.
9. Isolate sensitive sections of code to minimize exposure and potential damage from breaches.
10. Build a responsive incident management plan to swiftly address security breaches when they occur.
Building a Security-Conscious Development Environment
Creating a development environment that prioritizes best practices for secure coding involves catering to multiple aspects of software creation processes. One of the most effective strategies is to implement a continuous education program that updates development teams on the latest security threats and trends. This ongoing training ensures teams possess the knowledge needed to address potential vulnerabilities in their code. Additionally, implementing security checkpoints within the development cycle allows security measures to be automated and seamlessly integrated into the workflow. This could be achieved through software tools and systems that can continuously scan code and alert developers to potential issues. Cross-functional collaboration is another cornerstone of best practices for secure coding, reinforcing the understanding that security is a collective responsibility, not just a task for security specialists. Each code review can become an opportunity for imparting security knowledge, cementing the significance of security within the team’s culture. Adopting these practices ensures a proactive response to security challenges, preparing applications to withstand evolving threats and safeguarding their longevity and reputation in the competitive software industry.
Encouraging Secure Code Development
Developing an environment that strictly follows best practices for secure coding fosters a culture of security awareness. By implementing policies that encourage secure coding from the ground up, organizations can help mitigate risks associated with insecure coding practices. Automated tools such as static analysis should be employed to continually inspect and report code vulnerabilities. Furthermore, cross-departmental communication should be encouraged to ensure that all members, from developers to stakeholders, are informed about security expectations. Best practices for secure coding not only improve the security posture of applications but also contribute to maintaining trust with users and clients. A culture rooted in these practices will inevitably enhance an organization’s ability to adapt to new challenges, as systemic thinking and preparedness become intuitive parts of the development process.
Summary: The Imperative of Secure Coding Practices
In conclusion, best practices for secure coding are essential in navigating the complex terrain of modern software development. Secure coding practices are necessary not only to prevent unauthorized access and safeguard sensitive information but also to maintain the integrity and reliability of software applications. By adhering to secure coding standards, developers position themselves against the myriad challenges posed by cyber threats. Secure coding practices involve continuous education, employing automated tools, regular security assessments, and a cohesive approach to incorporate security in every step of the software development lifecycle. In essence, secure coding is not merely a reactive response to immediate threats but a proactive strategy to design inherently secure applications. As the digital landscape continues to grow and evolve, maintaining a commitment to secure coding practices ensures that developers can meet and overcome the challenges of tomorrow with robust and reliable software solutions.