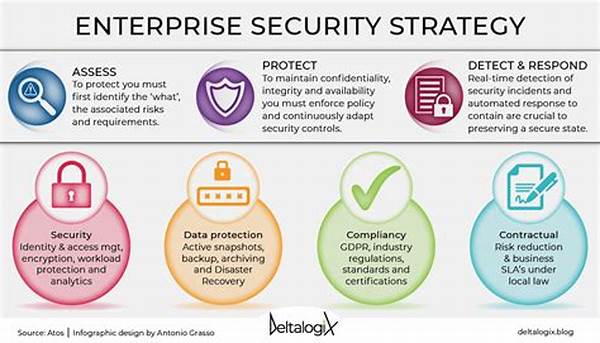
In the contemporary digital era, the proliferation of cyber threats poses significant challenges to organizations worldwide. The increasing frequency and sophistication of these threats necessitate robust cyber threat protection strategies. These strategies are imperative not only to safeguard sensitive information but also to ensure the continuity of business operations. Organizations must proactively adopt advanced measures to combat cyber threats effectively. Understanding and implementing comprehensive protection strategies can significantly mitigate risks associated with cyber incidents.
Read Now : Data Extraction Using Ai
Importance of Cyber Threat Protection Strategies
The importance of cyber threat protection strategies cannot be overstated in today’s interconnected world. Compliance with regulatory requirements often demands stringent cybersecurity measures, making sound strategies indispensable. The financial repercussions of cyber incidents further underscore the need for proactive measures. Firms are tasked with protecting sensitive data to maintain consumer trust and avoid legal liabilities. Developing a layered defense strategy becomes vital in this context, ensuring comprehensive protection.
Implementing effective cyber threat protection strategies aids in minimizing potential losses stemming from unauthorized data access or breaches. These strategies encompass various components, such as risk assessment, threat intelligence, and employee training. Regular system updates and vulnerability patches form the cornerstone of maintaining an organization’s defensive posture against evolving cyber threats. By adopting a multidimensional approach, entities can stay a step ahead of malicious actors, thereby safeguarding critical assets.
Moreover, fostering a culture of cybersecurity awareness through employee education is paramount to the success of these strategies. Employees serve as the first line of defense against cyber threats; thus, their understanding and attentiveness are crucial. Consistent training programs ensure that staff are equipped with the necessary knowledge to identify and report potential security incidents. Consequently, organizations can substantially reduce the risk of successful cyberattacks.
Key Elements of Cyber Threat Protection Strategies
1. Risk Assessment and Management: Conducting a thorough risk assessment forms the basis of effective cyber threat protection strategies. Identifying potential vulnerabilities and assessing their impact aids in formulating targeted defenses.
2. Threat Intelligence Gathering: Incorporating threat intelligence enables organizations to anticipate and counteract emerging cyber threats. Staying informed about the latest threat trends enhances an organization’s overall security posture.
3. Robust Access Controls: Implementing stringent access controls is crucial to ensuring that only authorized personnel have access to sensitive information, thus protecting against internal and external threats.
4. Comprehensive Incident Response Plan: An effective incident response plan details the steps to mitigate an attack swiftly, reducing its impact on operations and reputation.
5. Regular Training and Awareness Programs: Regular cybersecurity training ensures that employees are informed about potential threats and the correct procedures to prevent and respond to attacks.
Developing a Robust Cyber Threat Protection Framework
Constructing a robust cyber threat protection framework involves several critical phases. Initially, comprehensive risk assessment and threat identification form the bedrock of any security strategy. Organizations must meticulously evaluate their operating environment to uncover potential vulnerabilities and threats. This initial analysis facilitates the prioritization of risk, enabling the formulation of targeted strategies for mitigation.
Further, the integration of advanced technologies is instrumental in enhancing an organization’s defensive capabilities. Implementing layers of security technologies such as firewalls, intrusion detection systems, and antivirus software is crucial. These technologies work collectively to shield the organization from potential intrusions and disruptions. Moreover, automation plays a key role in maintaining vigilance around the clock. Automated systems enable real-time threat detection and response, thus bolstering an organization’s ability to withstand cyber threats.
Challenges in Implementing Cyber Threat Protection Strategies
Developing effective cyber threat protection strategies is not without its challenges. One primary obstacle is the ever-evolving nature of cyber threats, which continuously tests the resilience of existing security measures. Organizations often face difficulty in keeping pace with the latest tactics employed by cybercriminals. Consequently, maintaining an up-to-date and robust defense mechanism remains a formidable task. To address these challenges, organizations must invest in ongoing threat intelligence and adaptive security measures that can evolve in response to emerging threats.
Another significant challenge is the complexity of protecting diverse, distributed, and interconnected systems. As enterprises expand and embrace cloud technologies, their attack surface broadens, making comprehensive protection increasingly challenging to implement. In addition, the integration of new security technologies into existing frameworks can present compatibility issues. Organizations must carefully navigate these complexities to build a cohesive security posture that effectively protects vital assets.
Read Now : Bibliometrics In Interdisciplinary Research
Financial constraints are another barrier often encountered by organizations seeking to develop robust cyber threat protection strategies. Allocating sufficient resources towards comprehensive cybersecurity measures can be challenging, especially for smaller enterprises with limited budgets. To overcome this, organizations should perform cost-benefit analyses to prioritize investments that yield the highest level of protection relative to expenditure. Additionally, partnerships with external security providers can offer cost-effective solutions that enhance a company’s security capabilities.
Implementing Cyber Threat Protection Strategies in Complex Environments
In complex technological environments, deploying effective cyber threat protection strategies is essential. It requires a clear understanding of an organization’s specific security requirements and potential vulnerabilities. Architectural complexity and diversity present unique security challenges, necessitating tailored approaches to threat protection. Organizations must employ a risk-based approach to identify critical assets and prioritize protection accordingly.
Adopting advanced technologies, such as AI and machine learning, can significantly enhance detection and response capabilities. These technologies enable organizations to handle vast amounts of data and identify potential threats with greater precision. By automating threat detection and incorporating predictive analytics, companies gain a competitive edge in maintaining a proactive security stance. Collaboration across cross-functional teams is also essential in deploying strategies that encompass technology, processes, and policies.
Furthermore, maintaining comprehensive visibility over network traffic and system logs is crucial for effective monitoring and threat detection. By leveraging Security Information and Event Management (SIEM) systems, organizations can aggregate and analyze security data, enabling rapid threat identification. Creating an integrated approach ensures that threat protection strategies account for the entire security lifecycle—from prevention to detection and response—within complex environments.
Enhancing Cyber Threat Protection Through Proactive Measures
To bolster cyber threat protection strategies, organizations should employ proactive measures tailored to their specific threat landscape. Regular penetration testing and vulnerability scanning are fundamental to identifying potential security gaps before they can be exploited by malicious actors. These exercises enable organizations to anticipate potential threats and adapt their defensive measures accordingly.
Furthermore, securing remote access protocols is a vital aspect of proactive threat protection. As remote work becomes increasingly common, safeguarding access points against unauthorized intrusions is paramount. Employing multi-factor authentication and encrypted communication channels can significantly fortify remote connections. By implementing these measures, organizations enhance their resilience against potential cyber threats that exploit remote access vulnerabilities.
Moreover, collaborating with cybersecurity experts and engaging in information-sharing initiatives can provide valuable insights into emerging threat trends. Sharing threat intelligence within industry networks facilitates a collective defense approach, enabling organizations to fortify their strategies against common adversaries. By maintaining an awareness of industry-specific threats and learning from peers, organizations can continually refine and strengthen their cyber threat protection strategies.
Conclusion: Strengthening Cyber Resilience
In conclusion, the establishment of comprehensive cyber threat protection strategies is critical to fortifying an organization’s resilience against a range of digital threats. By adopting a multidimensional approach that encompasses risk assessment, advanced technologies, and continuous employee training, organizations can effectively safeguard their operations. Despite facing challenges such as evolving threats and resource constraints, organizations can overcome these with adaptive and proactive measures.
A robust cyber threat protection strategy not only safeguards critical data but also ensures business continuity, thereby protecting an organization’s reputation and stakeholder trust. As the cyber threat landscape evolves, organizations must remain vigilant and committed to refining their security strategies. By fostering a culture of cybersecurity awareness and leveraging cutting-edge technologies, entities can maintain a robust defense against the ever-growing spectrum of cyber threats.