In the contemporary technological landscape, Application Programming Interfaces (APIs) have become a crucial element for enabling communication between different software systems. As APIs facilitate the exchange of data between applications, ensuring data security has become of paramount importance. The security of data transmitted through APIs must be upheld to protect sensitive information and maintain trust. This article delves into various aspects of data security in API usage, highlighting the importance of secure API design, implementation, and management practices.
Read Now : Alternative Metrics For Research Impact
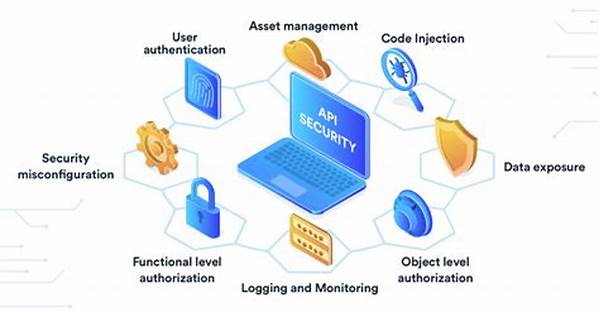
Importance of Data Security in API Usage
Data security in API usage is critical to safeguarding sensitive information from unauthorized access and cyber threats. One of the main reasons for ensuring data security in these interfaces is to prevent data breaches involving confidential information. Security protocols in APIs must be rigorously designed to incorporate authentication, encryption, and access control, ensuring that data is accessible only to authorized systems and users. The implementation of robust data security measures is vital to protect against attacks such as man-in-the-middle, where data is intercepted during transmission. Additionally, compliance with industrial and governmental data security standards is fundamental in managing and mitigating risks associated with data vulnerabilities in APIs. Neglecting data security in API usage can lead to substantial financial losses, reputational damage, and legal penalties for organizations that fail to protect user data. Therefore, adopting a proactive approach to data security fosters a secure data exchange environment, bolstering trust among users and stakeholders.
Key Components of Data Security in API Usage
1. Authentication: Verifying the identity of users and applications involved in data exchanges is essential. Authentication mechanisms like OAuth and OpenID Connect play a pivotal role in data security in API usage.
2. Encryption: Encrypting data both in transit and at rest ensures that even if intercepted or accessed without permission, the data remains unreadable to unauthorized parties.
3. Access Control: Implementing role-based access and authorization limits data exposure to only those with predefined entitlement, which is crucial for ensuring data security in API usage.
4. Rate Limiting: By restricting the number of API requests made within a certain timeframe, rate limiting defends against Denial of Service (DoS) attacks aimed at disrupting service availability.
5. Audit Logging: Maintaining detailed logs of API interactions offers a forensic trail to track data access and can help identify anomalies or breaches, thus reinforcing data security in API usage.
Challenges in Ensuring Data Security in API Usage
In navigating the complexities associated with data security in API usage, organizations face several challenges. A significant challenge is addressing diverse security threats that continually evolve with technological advancements. The need to adapt quickly to these evolving threats while ensuring the existing architecture remains secure is critical. Moreover, integrating security measures seamlessly into the API lifecycle is another challenge. This requires organizations to balance security without hindering the functional performance of APIs. Ensuring proper credential management, such as secure storage and protection of API keys, is another aspect requiring constant attention. Compromised credentials pose significant risks, further complicating data security. Additionally, achieving compliance with ever-changing regulatory requirements across different regions adds another layer of complexity, compelling organizations to align their API security practices with legal obligations.
Strategies to Enhance Data Security in API Usage
1. Implementing Robust Authentication Protocols: Strengthening authentication methods to verify API users enhances data security in API usage by limiting access to authorized entities only.
2. Regular Security Audits and Testing: Conducting frequent security assessments and penetration testing helps identify vulnerabilities and reinforce defenses within API infrastructures.
3. Adopting Encryption Best Practices: Utilizing strong encryption standards for data communication acts as a safeguard against data breaches, maintaining confidentiality and integrity.
4. Integrating Access Control Policies: By implementing stringent access controls and permissions, organizations protect APIs from unauthorized data access, crucial for data security in API usage.
5. Educating Stakeholders on Security Protocols: Regular training and awareness programs for developers and users ensure everyone understands the importance of maintaining data security in API usage.
Read Now : Aligning Formative And Summative Assessment Goals
6. Utilizing API Gateways: API gateways provide an additional layer of security, including functionalities like rate limiting and logging, boosting data security in API usage.
7. Monitoring and Anomaly Detection: Advanced monitoring systems can detect suspicious activities and anomalies, enhancing data security through proactive incident response.
8. Implementing Rate Limiting and Throttling: These techniques prevent abuse and overuse, often indicative of malicious attacks, thus safeguarding data security in API usage.
9. Utilizing Web Application Firewalls (WAFs): WAFs can filter and monitor HTTP traffic to and from an API, providing an additional security layer to prevent data breaches.
10. Ensuring Compliance with Security Standards: Aligning API practices with recognized security standards and regulations ensures a structured approach to maintaining data security in API usage.
Implementing Best Practices for Data Security in API Usage
Organizations striving to enhance data security in API usage must adhere to industry best practices, embedding security throughout the API lifecycle. Standard practices, such as designing APIs with security by default and incorporating security measures early in the development phase, are crucial. A well-thought-out API security strategy encompasses the end-to-end processes, including design, deployment, monitoring, and maintenance phases. Continuous monitoring of API environments is critical for identifying and responding to security incidents promptly. Deploying automated tools that track API activities can yield insights into potential vulnerabilities and breaches in real-time, enabling a swift response.
Furthermore, collaboration across teams enhances data security in API usage by integrating diverse perspectives and expertise. This interdisciplinary approach promotes the implementation of comprehensive security measures that address potential gaps in API systems. Engaging with stakeholders, including developers, IT security personnel, and management teams, ensures alignment toward common security goals. Additionally, it is essential to cultivate a culture of security awareness, providing ongoing training to equip employees with the knowledge needed to navigate emerging threats and best practices in API security.
The Future of Data Security in API Usage
As the digital landscape continues to evolve, so too will the strategies surrounding data security in API usage. Anticipated advancements in artificial intelligence and machine learning will likely introduce innovative security solutions capable of predicting and countering complex threats, ultimately fortifying API systems. The integration of AI-based anomaly detection systems holds promise for swiftly identifying and neutralizing suspicious activities, reducing the risk of data breaches. Collaborative efforts within the technology community to establish unified standards and share insights will play a pivotal role in advancing API security. By fostering a collective commitment to data security in API usage, organizations worldwide can proactively address emerging challenges, ensuring the protection of sensitive information across interconnected systems.
Summary: Data Security in API Usage
In summary, data security in API usage is a multifaceted challenge that necessitates a comprehensive and proactive approach. By implementing strong authentication mechanisms, encryption protocols, and rigorous access controls, organizations can significantly enhance the security of their API ecosystems. Moreover, ongoing monitoring and the use of advanced anomaly detection tools are vital in ensuring the early detection and response to potential threats. Organizations must remain agile, continually updating and refining their security strategies to keep pace with the rapidly evolving threat landscape.
The future of data security in API usage will be shaped by technological advancements, regulatory changes, and industry collaboration. As new technologies emerge, organizations should be prepared to adopt innovative security solutions and establish partnerships with industry peers to share knowledge and best practices. Through concerted efforts and a steadfast commitment to security, it is possible to create a resilient API environment that not only protects sensitive data but also fosters trust and confidence among users and stakeholders alike.