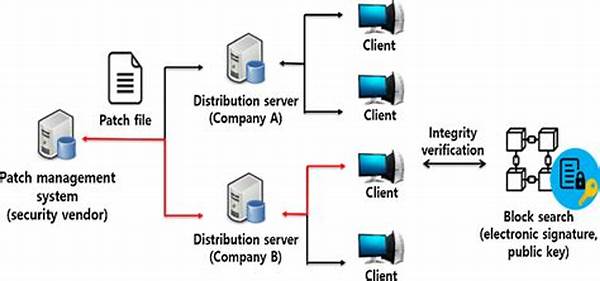
In an era where technology permeates every facet of our daily lives, ensuring the integrity of devices becomes a paramount concern. Device integrity verification processes are critical in safeguarding the functionality, security, and reliability of devices employed in various sectors. This article delves into the intricacies and importance of device integrity verification processes, ensuring that they serve as the cornerstone for maintaining the highest standards of operational excellence.
Read Now : Best Practices In Microservices Ci
The Importance of Device Integrity Verification
Device integrity verification processes are instrumental in establishing trust in the digital age. These processes serve as the backbone for ensuring that devices—be it smartphones, tablets, or critical infrastructure—operate as intended, free from compromise or malfunction. Given the ubiquitous nature of devices, the implications of a breach of integrity can be far-reaching, culminating in financial loss, reputational damage, and operational disruptions.
The primary aim of device integrity verification processes is to authenticate the components and functionalities of a device, thereby ensuring its compliance with predetermined standards and specifications. Such processes encompass a comprehensive set of examinations and tests to confirm that no unauthorized alterations have occurred. Consequently, these measures play a vital role in fortifying security measures, averting potential vulnerabilities, and safeguarding data intrinsic to organizational and individual success.
Furthermore, device integrity verification processes contribute to enhancing consumer confidence in technological products. For manufacturers, implementing these processes in their production lines signifies a commitment to quality and reliability. Consumers, then, are assured of the authenticity and safety of the devices they interact with, fostering a sense of security and trust in brand offerings.
Key Components of the Verification Process
1. Device integrity verification processes encompass hardware inspection, ensuring all physical components meet original specifications.
2. Software audits are integral, analyzing code and applications to detect anomalies or unauthorized interventions within the device.
3. Encryption assessments verify the robustness of cryptographic protocols safeguarding data integrity during device integrity verification processes.
4. Firmware checks ensure that installed firmware is authentic and has not been manipulated, thereby maintaining device integrity.
5. Continuous monitoring and real-time alerts are necessary for preemptive detection of integrity breaches in device integrity verification processes.
Challenges in Implementing Verification Processes
The implementation of device integrity verification processes is fraught with inherent challenges. One of the primary obstacles is the rapidly evolving nature of technology, where malefactors continuously develop sophisticated techniques to circumvent security measures. Therefore, verification processes must be dynamic and adaptable to counter emerging threats.
Another pertinent challenge is the complexity involved in integrating device integrity verification processes into existing systems, particularly within large organizations. These processes require a meticulous alignment of technological resources, skilled personnel, and financial investment, which may act as deterrents for smaller entities. Additionally, ensuring that verification methods align with international standards and regulations necessitates exhaustive compliance checks, further complicating the implementation landscape.
Nonetheless, these challenges, while significant, should not deter organizations from investing in robust device integrity verification processes. The long-term benefits, notably in risk mitigation and brand reputation enhancement, far outweigh the initial hurdles encountered in their deployment. A proactive approach to overcoming these challenges can lead to the establishment of a resilient technological infrastructure, pivotal for sustained growth.
Verification Strategies
1. Device integrity verification processes begin with creating comprehensive verification protocols, establishing a structured approach tailored to specific device requirements.
2. Regular updates to verification measures are essential, reflecting the evolving nature of potential threats to device integrity.
3. Collaboration with industry experts enhances verification processes, integrating specialist knowledge into the standard procedures.
4. Employing artificial intelligence in device integrity verification processes can significantly improve detection accuracy and efficiency.
5. User education plays a crucial role, empowering users with awareness and proactive measures to maintain device integrity.
Read Now : Machine Learning In Water Scarcity Management
6. Cross-industry partnerships facilitate the sharing of best practices, enriching device integrity verification processes.
7. Adoption of blockchain technology offers immutable records, aiding in authenticating and verifying device components.
8. Root cause analysis of past breaches informs better device integrity verification processes, preventing recurrence.
9. Vendor assessments ensure third-party components adhere to integrity standards, vital within device integrity verification processes.
10. Continuous feedback loops from device users to manufacturers enhance device integrity verification processes through real-world data applications.
Integrating Processes into Organizational Frameworks
Incorporating device integrity verification processes into organizational frameworks demands a multifaceted approach that aligns with an organization’s strategic objectives. Initially, establishing a dedicated task force focused on device integrity is crucial in overseeing the seamless integration of these processes. This task force should comprise cross-departmental representatives, thereby ensuring a holistic integration that addresses technological, operational, and security aspects.
Successful integration of device integrity verification processes also necessitates a thorough audit of existing workflows and infrastructures. By assessing current practices, organizations can identify potential gaps and areas for improvement in their verification strategies. Furthermore, investing in cutting-edge technology solutions that facilitate automation and real-time analysis is imperative for maintaining the efficacy and efficiency of these processes. This investment, while substantial, yields significant returns by fortifying the organization’s defenses against integrity breaches.
Moreover, fostering a culture of continuous improvement and adaptation within organizations is instrumental in preserving the relevance of device integrity verification processes. Regular training and awareness programs should be conducted to ensure that employees remain abreast of new threats and verification techniques. These initiatives, coupled with a commitment to maintaining dynamic processes, empower organizations to anticipate and respond effectively to integrity challenges, thus securing a competitive advantage in their respective industries.
Benefits of Robust Verification Systems
Device integrity verification processes serve as a bulwark against threats, offering substantial benefits that extend beyond mere protection. Creating a robust verification system helps prevent security breaches, thereby safeguarding sensitive data and critical operations. It instills confidence among stakeholders, including customers, investors, and regulatory bodies, that the organization prioritizes integrity within its technological ecosystem.
Moreover, integrating stringent device integrity verification processes enhances operational efficiency by preemptively identifying and rectifying potential weaknesses before they escalate into significant issues. This proactive approach reduces the likelihood of downtime or disruptions, ensuring the continuity of essential services. The adoption of robust verification measures can also lead to cost savings in the long term, as it mitigates the financial repercussions associated with data breaches, system failures, and subsequent reputational damage.
Finally, organizations that prioritize device integrity verification processes position themselves as leaders in their sectors, gaining a competitive advantage through the trust and reliability they offer to their clients. Such organizations are often viewed as exemplars of technological innovation and responsibility, thereby fostering enhanced brand loyalty and customer satisfaction. The cultivation of this reputation can open doors for business expansion and collaborations, further solidifying their standing within the global marketplace.
Summary of Integrity Processes
In summation, device integrity verification processes are a cornerstone in securing technological advancements and are set to play an increasingly pivotal role as reliance on devices continues to surge. By embracing these processes, companies are committing to the rigorous safeguarding of both their assets and their customers’ data, thus fortifying their overall security posture.
Device integrity verification processes ensure that the promise of technology—its convenience, connectivity, and immense potential—is delivered without compromise. As cyber threats grow in sophistication, the onus rests on organizations to adapt and enhance their verification strategies continuously. By doing so, they do not merely respond to threats but anticipate and preempt them, safeguarding their long-term sustainability and success.