The modern landscape of digital interaction necessitates robust mechanisms for secure and efficient access management. At the forefront of these mechanisms is OAuth, a prevailing open standard for access delegation. Implementing OAuth access tokens, a central component of the OAuth protocol, is pivotal in granting and managing permissions without compromising user credentials. The sophistication of OAuth tokens lies in their ability to enable third-party applications to interact securely on a user’s behalf, facilitating seamless and secure inter-application communication.
Read Now : Leveraging Ai For Faster Discoveries
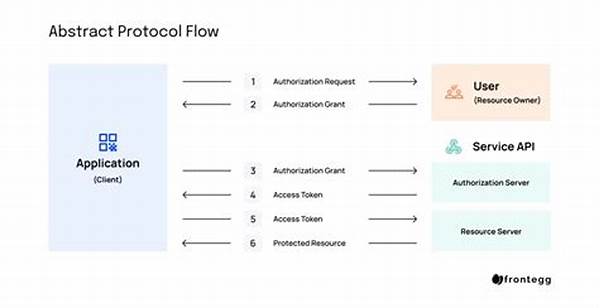
Understanding OAuth Access Tokens
Implementing OAuth access tokens involves an intricate process designed to enhance both security and functionality. These tokens are essential instruments in the broader OAuth framework, acting as temporary keys that authorize specific access levels without sharing passwords. OAuth tokens reduce vulnerabilities associated with credential sharing by ensuring that applications only gain permissions explicitly granted by the user. Moreover, the revokable nature of tokens adds an additional layer of security, allowing users to withdraw permissions if a token is compromised. Thus, the implementation of OAuth access tokens is a crucial step in fostering a secure and user-centric digital environment.
OAuth tokens streamline the interaction between users and applications, predominantly by decoupling authentication from authorization. When implementing OAuth access tokens, an application receives a token post user consent, signaling its right to access resources for a limited duration and scope. This tokenized authorization model alleviates the need for direct password sharing, ensuring that user credentials remain confidential even during cross-platform engagements. Additionally, the expiration of tokens means that any breach in security is ephemeral, providing a self-mitigating form of access control. Hence, implementing OAuth access tokens ensures a more secure and user-friendly approach to digital authentication and authorization.
Benefits of Implementing OAuth Access Tokens
1. Enhanced Security: Implementing OAuth access tokens significantly bolsters security by substituting direct credential sharing with temporary tokens, minimizing exposure of user information and reducing the threat surface.
2. User Control: OAuth access tokens offer robust user-driven permission settings, empowering users with the ability to grant and revoke application access at any time without altering their primary credentials.
3. Seamless Interoperability: The implementation of OAuth access tokens allows applications to seamlessly access user resources across different platforms and services, fostering a more integrated user experience.
4. Scalability: Implementing OAuth access tokens facilitates scalable operations by enabling effortless integration of new applications and services, allowing for efficient resource management.
5. Privacy Preservation: OAuth access tokens empower privacy by ensuring that applications only receive pertinent user information necessary for operation, thereby protecting user data integrity during digital communications.
Challenges in Implementing OAuth Access Tokens
The process of implementing OAuth access tokens is not devoid of challenges. Chiefly among these challenges is ensuring the secure storage and exchange of tokens across various platforms. Tokens, if intercepted, can be exploited by malicious entities to gain unauthorized access. Implementers must hence focus on protecting tokens through encrypted storage and secure transmission protocols. Furthermore, the precise implementation of token lifecycles—specifying expiration and renewal—requires careful configuration to balance accessibility and security. Consequently, crafting a meticulous framework when implementing OAuth access tokens is critical to safeguarding digital interactions without sacrificing functionality.
Furthermore, the complexity involved in managing user consent during the OAuth flow presents another substantial challenge. Implementing OAuth access tokens demands an intuitive user interface that clarifies the permissions being requested. An effective interface will ensure that users understand the scope and limitations of access being granted, thus maintaining transparency and trust. Additionally, the integration of thorough logging mechanisms is essential to monitor token usage and detect any anomalies swiftly. By addressing these challenges, organizations can ensure that the implementation of OAuth access tokens meets both security prerequisites and user expectations.
Practical Considerations in Implementing OAuth Access Tokens
1. Token Encryption: Enhancing token security through encryption is critical in implementing OAuth access tokens to prevent unauthorized access and ensure data integrity.
2. Expiration Management: Effective management of token expiry ensures that tokens remain operationally relevant and secure without unnecessary risk exposure.
3. Token Scope Definition: Implementing OAuth access tokens requires precise definition of token scopes to limit access strictly to necessary resources, reducing potential misuse.
4. User Interface Design: A well-designed interface eases user consent, clarifying the permissions being granted during the OAuth process.
Read Now : Database Schema Design Best Practices
5. Revocation Mechanisms: Providing users with easy token revocation options enhances security, allowing for prompt mitigation in case of potential compromise.
6. Cross-Site Request Forgery (CSRF) Protection: When implementing OAuth access tokens, CSRF protection is paramount to defend against unauthorized token trades.
7. Logging and Monitoring: Comprehensive monitoring of token usage detects anomalies and misuse, safeguarding against unauthorized access.
8. Multi-factor Authentication (MFA): Coupling OAuth implementations with MFA enhances security, adding an additional verification layer.
9. Refresh Token Utilization: Refresh tokens enable secure token regeneration, reducing the need for frequent reauthentication processes.
10. Compatibility and Standards Compliance: Ensuring compliance with OAuth standards and compatibility across platforms is crucial in maintaining security integrity while implementing OAuth access tokens.
Conclusion and Future Outlook
The dynamics of digital authorization continue to evolve, with OAuth access tokens playing a crucial role in shaping secure authentication practices. Implementing OAuth access tokens stands as a fundamental component in enforcing robust security protocols in digital ecosystems. As technological advancements introduce new attack vectors, the importance of refining token implementation strategies becomes increasingly evident. Organizations are encouraged to continuously assess and update their OAuth protocols, ensuring that they align with the latest security standards and address emerging vulnerabilities.
Looking forward, the adoption of more sophisticated AI-driven security analysis tools is likely to further enhance the robustness of OAuth implementations. These tools will assist in scrutinizing token activity, detecting anomalies, and predicting potential threats. As part of a proactive security strategy, organizations must prioritize education and training for developers involved in implementing OAuth access tokens, ensuring a comprehensive understanding of both the capabilities and limitations of OAuth. In sum, the judicious application of OAuth access tokens remains central to a future where digital interactions are secure, efficient, and trust-based.
Implementing OAuth Access Tokens: Key Takeaways
Implementing OAuth access tokens is integral to modern application security frameworks, offering improved interaction and access configuration. It underscores a shift from traditional credential sharing to a more sophisticated token-based system, emphasizing user-centric control and enhanced privacy actions. Organizations embarking on implementing OAuth access tokens must prioritize security considerations, ensuring encrypted token storage, secure exchanges, and meticulous lifecycle management. Additionally, incorporating intuitive user interfaces and comprehensive logging mechanisms significantly fortifies the security landscape, facilitating seamless and secure authorization transactions.
Furthermore, strategic alignment with OAuth standards ensures compatibility across diverse digital platforms, promoting interoperability. With the ever-growing digital interactions, implementing OAuth access tokens as part of an intelligent security regimen fosters trust and efficiency, ultimately contributing to a secure digital experience. In light of emerging technological challenges and opportunities, continued investment in smart security practices, developer education, and emerging technology integration will be essential to maximize the benefits of OAuth implementation. As the digital domain expands, OAuth’s role is set to grow, cementing its place as a cornerstone of future-proof digital security.