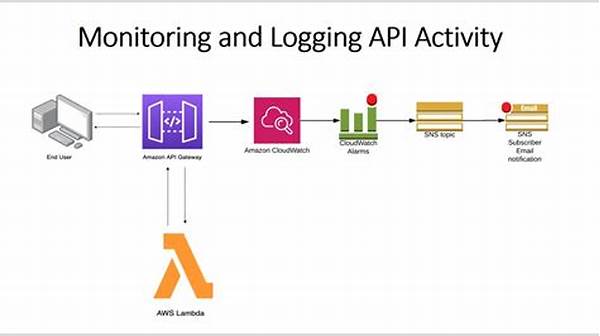
In the realm of modern digital infrastructure, the monitoring and logging of API access attempts hold paramount significance for maintaining security and operational integrity. APIs, as integral components of software architecture, serve as gateways to valuable data and services. As such, they are often targets for unauthorized access and potential breaches. Hence, establishing robust mechanisms to monitor and log these access attempts becomes essential in safeguarding sensitive information and ensuring compliance with regulatory standards.
Read Now : Legacy Systems Data Conversion Tips
The Importance of Monitoring and Logging API Access Attempts
The significance of monitoring and logging API access attempts cannot be overstated. It is a practice that facilitates the identification of suspicious activities, such as repeated failed login attempts or access requests from unexpected geographical locations. By meticulously documenting each API access attempt, organizations can establish a comprehensive audit trail, which is invaluable for retrospective investigations and forensic analysis. Moreover, such a logging practice aids in assessing the API’s performance, enabling the identification and mitigation of bottlenecks or potential vulnerabilities within the system. Consequently, monitoring and logging efforts contribute to an organization’s overarching cybersecurity posture and operational efficiency.
Furthermore, compliance with legal and regulatory frameworks often mandates the documentation of access attempts to sensitive data. Monitoring and logging of API access activities ensure adherence to such requirements, thereby avoiding potential legal repercussions and enhancing trust with stakeholders. By implementing continuous monitoring systems, organizations can generate real-time alerts that prompt immediate corrective actions against unauthorized access attempts, safeguarding the integrity and confidentiality of information assets. In essence, effective monitoring and logging strategies serve as both a preventive measure against potential threats and a tool for enhancing organizational efficiency.
Implementing Monitoring and Logging API Access Attempts
1. Framework Selection: Select an appropriate monitoring and logging framework that integrates seamlessly with existing systems, ensuring efficient tracking of API access attempts.
2. Data Collection: Gather detailed information about each access attempt, including timestamp, request origin, and user credentials, to create a comprehensive audit log.
3. Alert Mechanisms: Establish real-time alert systems to notify administrators of abnormal patterns in access attempts, allowing for swift intervention.
4. Compliance Assurance: Ensure that the monitoring and logging practices align with relevant legal and regulatory standards, safeguarding against non-compliance issues.
5. Regular Audits: Conduct periodic audits of the logs to analyze trends, identify potential vulnerabilities, and implement necessary improvements to the security framework.
Challenges in Monitoring and Logging API Access Attempts
Despite the undeniable benefits, the monitoring and logging of API access attempts present several challenges. One of the primary difficulties lies in handling the sheer volume of data generated from numerous access attempts, particularly in large-scale operations. Efficient data management and analysis systems are required to extract meaningful insights without overwhelming IT resources. Additionally, the sophistication of cyber threats is constantly evolving, necessitating adaptive monitoring technologies capable of identifying and mitigating novel attack vectors promptly.
Organizations must also address the potential privacy concerns arising from the collection and storage of access logs, ensuring compliance with privacy regulations and safeguarding user data. Implementing encryption and anonymization techniques can mitigate risks associated with data breaches. Lastly, establishing a culture of continuous monitoring and improvement, supported by a skilled workforce, is crucial to overcoming these challenges effectively.
Strategies for Enhancing Monitoring and Logging API Access Attempts
1. Anomaly Detection: Utilize machine learning algorithms to automatically detect anomalies in access patterns, which may indicate security threats.
2. Integration with SIEM: Integrate API monitoring systems with Security Information and Event Management (SIEM) platforms for a centralized view of security events.
3. User Access Management: Implement stringent access controls and regularly update user permissions to minimize unauthorized access attempts.
4. Encryption and Security: Use encryption to protect sensitive data within logs, ensuring integrity and confidentiality.
Read Now : Implementing Ssl/tls For Apis
5. Advanced Analytics: Employ advanced analytics tools to derive actionable insights from the access logs, facilitating proactive security measures.
6. Training and Awareness: Provide regular training to staff on security best practices and the importance of monitoring and logging in protecting organizational assets.
7. Redundancy and Backup: Ensure redundancy and backup systems for logs to prevent data loss and support disaster recovery efforts.
8. Data Retention Policies: Define clear data retention policies outlining the duration for keeping logs, aligned with compliance requirements.
9. Scalability Solutions: Adopt scalable solutions to accommodate growing data volumes as API usage expands.
10. Continuous Improvement: Establish a feedback loop for continuous improvement of monitoring and logging practices, informed by audit outcomes and technological advancements.
Achieving Excellence in Monitoring and Logging API Access Attempts
In striving for excellence in monitoring and logging API access attempts, organizations must prioritize a comprehensive approach that encompasses technology, compliance, and human factors. Investing in state-of-the-art tools and solutions that leverage artificial intelligence and machine learning can greatly enhance the detection and prevention of unauthorized access attempts. However, the technological aspect should be complemented by a robust policy framework that ensures compliance with evolving cybersecurity and privacy standards.
Furthermore, fostering a culture that emphasizes transparency and accountability in access management is vital to achieving long-term success. This includes regular training programs and awareness campaigns to boost the workforce’s ability to recognize and react to potential threats effectively. By integrating these practices into the organization’s operational fabric, a resilient monitoring and logging ecosystem can be cultivated, providing a formidable defense against unauthorized API access attempts and a foundation for sustained security and operational excellence.
Conclusion of Monitoring and Logging API Access Attempts
In conclusion, monitoring and logging API access attempts are critical components of a comprehensive cybersecurity strategy, essential for protecting sensitive information and maintaining operational integrity. By meticulously documenting access attempts and analyzing these logs, organizations can strengthen their security posture, ensuring timely responses to potential threats. Moreover, these practices facilitate compliance with regulatory standards, mitigate legal risks, and uphold stakeholder trust by demonstrating a commitment to data protection and regulatory adherence.
The challenges associated with monitoring and logging API access attempts, including data volume management and evolving threat landscapes, necessitate a strategic and dynamic approach. Organizations must leverage advanced technologies, prioritize employee training, and maintain a culture of continuous monitoring and improvement to effectively address these challenges. By doing so, they can build a resilient infrastructure capable of withstanding emerging threats and securing their API ecosystems for the future.