In the modern digital ecosystem, ensuring secure communication between clients and servers is of paramount importance. One of the most reliable methods to achieve this is through REST API token-based authentication. This technique enables the identification and authorization of users attempting to access data or services over the network. In this article, we will delve deeply into the concept of REST API token-based authentication, addressing its core features, working mechanism, and advantages. Understanding this authentication method is crucial for developers aspiring to secure RESTful services effectively and efficiently.
Read Now : Current Developments In Journal Analytics
Understanding REST API Token-Based Authentication
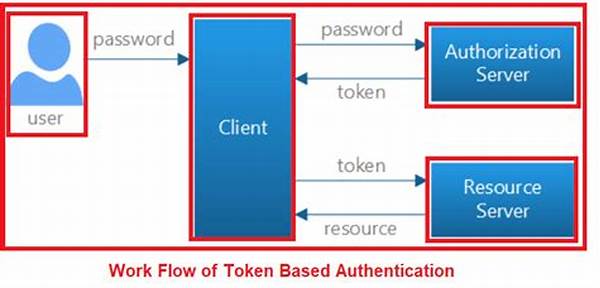
REST API token-based authentication is a method used to validate the identities of users attempting to access resources on a server. Upon successful login, the server issues a token, a string of encrypted data, which acts as a passcard for the user. Instead of re-entering their credentials for each request, users provide the token, simplifying the authentication process. This system is widely favored due to its flexibility and efficiency in managing user sessions across diverse digital platforms.
The tokens, typically generated following a handshake or secure login process, carry encoded information, allowing the server to decipher and authenticate the requesting entity. As digital operations continue to grow, REST API token-based authentication stands out as a robust solution for controlling and verifying access rights. Whether it’s for mobile apps, web services, or IoT devices, this token-centric mechanism ensures that the right users gain access to specific resources, mitigating unauthorized interactions and enhancing data security.
Key Features of REST API Token-Based Authentication
Implementation of REST API Token-Based Authentication
The implementation of rest API token-based authentication begins with a user login operation. Upon entering valid credentials, the server generates a unique token that contains encoded information about the user’s identity and rights. This token is issued to the client and must accompany subsequent requests to secure server resources. Each request header should include the token for the server to authenticate and respond appropriately. Integration of this authentication protocol across diverse applications enables secure and seamless user experiences.
Furthermore, REST API token-based authentication often relies on protocols such as JSON Web Tokens (JWT) or OAuth 2.0 for token creation and validation. These protocols standardize the encoding and exchange of tokens, thus enabling seamless interoperability and enhanced security. The server verifies the token’s authenticity using its secret or public key, ensuring that only valid tokens gain resource access. Overall, this method provides a scalable and reliable solution for managing extensive user authentication across varied digital environments.
Advantages of REST API Token-Based Authentication
1. Enhanced User Experience: By eliminating the need for repeated credential submissions, rest API token-based authentication fosters a seamless user experience.
2. Increased Security: The implementation of token expiry and cryptographic validation significantly elevates the security level of data transmission.
3. Efficient Resource Management: Given its stateless attribute, this authentication method optimizes resource utilization on the server side.
Read Now : Water Resources And Climate Change
4. Cross-Platform Compatibility: The versatile nature of rest API token-based authentication ensures that it can be seamlessly integrated across different platforms.
5. Reduced Load on Servers: Stateless authentication enhances server performance by ensuring minimal resource retention for user sessions.
Challenges in REST API Token-Based Authentication
Despite its advantages, implementing REST API token-based authentication presents certain challenges that developers must address. Firstly, the security of token storage on the client side is critical. Tokens stored improperly can become potential targets for hackers. Furthermore, ensuring token confidentiality during transmission requires the consistent use of HTTPS. Failure to do so exposes tokens to potential interception and misuse. Implementing token refresh mechanisms is another essential aspect, as static or expired tokens can hinder the user experience and compromise security. thoughtful planning and strategic execution can mitigate these challenges, resulting in an effective authentication framework.
Conclusion: The Importance of REST API Token-Based Authentication
In conclusion, REST API token-based authentication is indispensable in today’s digital landscape due to its flexibility, security, and scalability. Employing token-based methods enables a robust authentication mechanism that aligns with the stateless principles of REST. Such an approach is crucial for applications that operate on various platforms and require seamless, secure communications between clients and servers. By ensuring data integrity and access control, rest API token-based authentication enhances both user confidence and platform reliability. As digital ecosystems continue evolving, understanding and implementing token-based authentication will remain vital for developers and organizations committed to maintaining secure and efficient digital services.