In today’s interconnected digital landscape, the security of information exchange is paramount. As the backbone of many online services, Application Programming Interfaces (APIs) facilitate complex interactions between software components. Thus, secure API connection protocols are indispensable in preserving the confidentiality, integrity, and availability of data. This article delves into the nuances of secure API connection protocols, offering insights into their significance and implementation.
Read Now : Rest Versus Soap Performance
The Importance of Secure API Connection Protocols
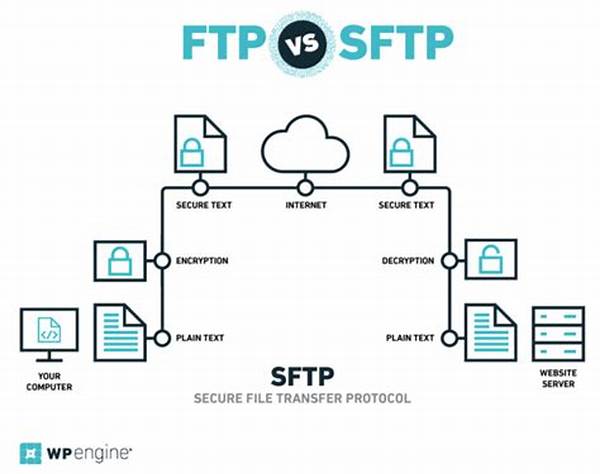
Secure API connection protocols are fundamental for ensuring that data transmitted across networks remains protected from unauthorized access and tampering. These protocols establish a secure communication channel, enabling systems to exchange sensitive information safely. The proliferation of cyber threats has heightened the need for robust security measures, making secure API connection protocols a critical component in the digital ecosystem. They employ encryption techniques to safeguard data, ensuring that information in transit remains confidential and is only accessible to intended recipients.
Moreover, authentication mechanisms embedded within these protocols verify the identity of entities attempting to access the API. This prevents unauthorized users from exploiting system vulnerabilities. Implementing secure API connection protocols is not merely a technical requirement but a strategic imperative that bolsters user trust and complies with regulatory mandates. While they vary in complexity and application, these protocols are unified in their goal to mitigate security risks, making them indispensable in the pursuit of resilient digital infrastructure.
Key Features of Secure API Connection Protocols
1. Encryption: Secure API connection protocols use encryption to protect data in transit, ensuring confidentiality and preventing unauthorized access.
2. Authentication: These protocols incorporate authentication methods to verify the identities of users and systems accessing the API.
3. Integrity Verification: Data integrity is maintained through mechanisms that detect any alterations during transmission.
4. Tokenization: Access tokens are utilized to manage API requests securely, minimizing the risk of unauthorized access.
5. Throttling and Rate Limiting: Protocols enforce usage limits to prevent abuse and ensure fair resource distribution among users.
Implementing Secure API Connection Protocols
Implementing secure API connection protocols requires a comprehensive understanding of the organization’s security architecture and requirements. It starts with selecting the appropriate protocol that aligns with the specific use case, such as OAuth for secure authorization or TLS for encrypting data streams. Establishing a framework for continuous monitoring and threat detection is essential to ensure that the security measures remain effective over time.
Regular audits and compliance checks are integral components of the implementation process, assuring adherence to industry standards. Additionally, educating stakeholders about best practices and potential vulnerabilities is vital in creating a security-aware culture. By adopting a proactive approach, organizations can anticipate security challenges, thus ensuring that their secure API connection protocols remain robust and adaptive to evolving cyber threats.
Practical Applications of Secure API Connection Protocols
Secure API connection protocols are vital in various sectors:
1. E-commerce: Protects customer data during online transactions.
2. Healthcare: Ensures patients’ confidential medical records are securely exchanged.
3. Financial Services: Safeguards sensitive financial information against breaches.
4. Social Media: Protects user data against unauthorized access.
Read Now : Whole-person Assessment Integration Techniques
5. Government: Guarantees secure communication of sensitive public data.
6. IoT Devices: Ensures safe data exchange between connected devices.
7. Cloud Computing: Secures data transfers between cloud services.
8. Education: Protects personal and academic records.
9. Telecommunications: Secures communication between networks.
10. Software Development: Protects intellectual property during API calls.
Challenges in Maintaining Secure API Connection Protocols
Maintaining secure API connection protocols in today’s ever-evolving digital landscape presents several challenges. The rapid advancement of technology results in constantly changing threat vectors that necessitate agile and responsive security measures. One significant challenge lies in keeping protocols updated to counteract newly emerging threats effectively. Ensuring compatibility between different systems and protocols can also pose a challenge, often requiring extensive testing and validation efforts.
Moreover, balancing security with performance remains a critical issue, as enhanced security measures can introduce latency and overhead that impact user experience. Organizations must also address the challenge of scaling security solutions to accommodate growing volumes of data and increasing numbers of API calls without compromising on security standards. Lastly, the human factor remains a persistent challenge, necessitating ongoing education and training to mitigate risks associated with human error and insider threats in implementing secure API connection protocols.
Strategic Considerations for Secure API Connection Protocols
Strategically implementing secure API connection protocols requires careful planning aligned with organizational objectives and regulatory requirements. Establishing stringent security policies and guidelines forms the foundation for maintaining robust protocols. Collaborations with cybersecurity experts can provide valuable insights into emerging threats and innovative security solutions. Organizations should prioritize investments in advanced technologies to enhance protocol capabilities and adapt to the dynamic cybersecurity landscape.
The integration of AI and machine learning technologies into security frameworks holds promise for enhancing threat prediction and adaptive response measures in real-time. Additionally, cultivating a culture of security awareness among all stakeholders, including development teams, users, and management, is crucial for reducing vulnerabilities attributable to human factors. By adopting a proactive, technology-driven, and user-centric approach, organizations can establish and maintain secure API connection protocols that fortify their digital ecosystems against ever-evolving cyber threats.
Conclusion
In conclusion, secure API connection protocols are integral to safeguarding digital interactions in an increasingly connected world. By leveraging robust encryption, authentication, and access control measures, these protocols play a pivotal role in protecting data and maintaining the integrity of online services. As technology continues to evolve, the importance of maintaining up-to-date secure API connection protocols cannot be overstated. They serve as the first line of defense against cyber threats, ensuring secure exchanges and fostering trust in digital transactions. Organizations must remain vigilant, continuously adapting their security strategies to ensure resilient and secure API connection protocols in the face of emerging challenges.
Secure API connection protocols are more than just technical specifications; they are strategic assets that enhance organizational security. By prioritizing the adoption and maintenance of strong secure API connection protocols, organizations can confidently navigate the complexities of the digital age, providing robust protection for their systems and users alike. Through a combination of technological innovation, strategic planning, and continuous education, the implementation of secure API connection protocols can be leveraged to achieve a secure and trustworthy digital environment for all stakeholders.