In the modern digital landscape, ensuring the security of data in transit is paramount. With the increasing reliance on Application Programming Interfaces (APIs) for data exchange, safeguarding sensitive information during transmission has become a critical concern. Secure API data transmission strategies play a vital role in protecting data from interception, unauthorized access, and potential breaches. By implementing robust security measures, organizations can mitigate risks and ensure the confidentiality and integrity of their data.
Read Now : Ecological Impact Of Resource Overuse
Importance of Secure API Data Transmission Strategies
In today’s interconnected world, secure API data transmission strategies have gained significant importance. As businesses rely heavily on APIs to facilitate communication between systems, it becomes imperative to establish secure channels for data exchange. These strategies involve implementing protocols and technologies such as HTTPS, OAuth, and encryption methods. By doing so, organizations can safeguard sensitive information from cyber threats and unauthorized access, ensuring that data integrity and confidentiality are maintained. Furthermore, secure API data transmission strategies instill confidence among consumers, reinforcing trust in the digital ecosystem. Businesses that prioritize these strategies are better equipped to protect their assets and adhere to regulatory requirements, ultimately fostering a safer and more reliable digital environment.
Key Components of Secure API Data Transmission Strategies
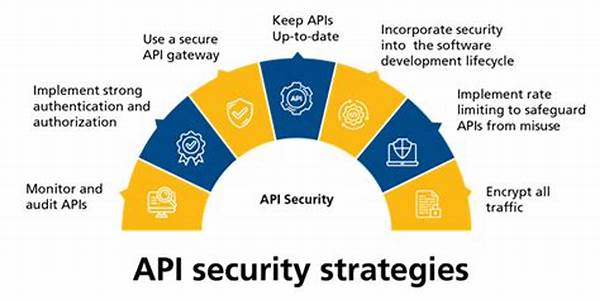
1. Encryption Protocols: Implementing strong encryption protocols is a fundamental aspect of secure API data transmission strategies. Encrypting data in transit ensures that unauthorized parties intercepting the data cannot decipher its contents, thereby safeguarding sensitive information.
2. Authentication Mechanisms: Secure API data transmission strategies encompass robust authentication mechanisms to verify the identities of users and systems. Techniques such as OAuth, API keys, and tokens are pivotal in ensuring that only authorized entities can access the API.
3. Transport Layer Security (TLS): TLS is a crucial component of secure API data transmission strategies, providing a secure communication channel between the client and the server. By encrypting the data exchanged, TLS prevents eavesdropping and tampering.
4. Data Integrity Checks: Implementing data integrity checks, such as checksums and message digests, is essential for secure API data transmission strategies. These checks ensure that data has not been altered during transit, maintaining its accuracy and reliability.
5. Rate Limiting and Throttling: Secure API data transmission strategies often incorporate rate limiting and throttling techniques to prevent abuse and mitigate denial-of-service (DoS) attacks. By controlling the number of requests a client can make, potential threats are minimized.
Challenges in Implementing Secure API Data Transmission Strategies
Despite the necessity of secure API data transmission strategies, several challenges impede their implementation. The dynamic nature of evolving cyber threats requires continuous adaptation and refinement of security measures. Organizations must stay abreast of changes in technology, regulations, and industry standards to remain resilient. Furthermore, the integration of security measures should be seamless, avoiding disruptions in API performance. Balancing security and usability is a crucial yet challenging aspect. Additionally, organizations must allocate appropriate resources to ensure the implementation and maintenance of secure API data transmission strategies. Overcoming these challenges requires a proactive approach, with organizations fostering a culture of security awareness and collaborating with cybersecurity experts to stay ahead in protecting their digital assets.
Best Practices for Secure API Data Transmission Strategies
1. Implement Strong Encryption Methods: Use advanced encryption algorithms such as AES to secure data, ensuring it remains protected during transmission.
2. Utilize Secure Communication Protocols: Employ protocols like HTTPS and TLS that provide a secure communication channel for data exchange, safeguarding against interception.
3. Regular Security Assessment and Audits: Conduct regular audits to identify vulnerabilities in API data transmission and implement necessary corrections to ensure continued security.
4. Employ Token-Based Authentication: Utilize tokens for authentication, ensuring only authorized users can access APIs, thereby enhancing security.
5. Monitor and Log API Activity: Keep track of API usage and unusual activities through logging, enabling the identification and response to potential threats.
6. Version Control and Update APIs Regularly: Maintain APIs through regular updates to fix vulnerabilities and enhance their security features.
Read Now : Climate Impact Mitigation Through Healthy Soils
7. Implement IP Whitelisting: Limit API access to trusted IP addresses only, thereby protecting against unauthorized access.
8. Sensitivity Data Handling: Ensure that sensitive data transmitted via APIs is minimized and handled with additional care to prevent security breaches.
9. User Education and Training: Educate users about security practices involved in using APIs to reduce the risk of human-related vulnerabilities.
10. Collaborate with Cybersecurity Experts: Work with security specialists to implement industry best practices in secure API data transmission strategies.
Implementing Secure API Data Transmission Strategies in Modern Enterprises
Enterprises today are increasingly dependent on APIs to enhance operational efficiency and facilitate seamless integration with third-party services. As such, implementing secure API data transmission strategies is no longer optional but essential for safeguarding sensitive data. Protecting data during transmission entails not only implementing encryption protocols and authentication mechanisms but also entails a commitment to continuous monitoring and threat assessment. It involves adopting a comprehensive approach that addresses every aspect of data exchange, from user authentication to server communication. By doing so, enterprises ensure their data remains protected against unauthorized access and cyber threats.
Moreover, secure API data transmission strategies demand careful consideration of emerging technologies and industry standards. Enterprises need to stay abreast of the latest advancements in encryption, authentication, and data protection to enhance their cybersecurity posture. This involves not only technical deployments but also fostering a culture of security awareness among employees, partners, and customers. Regular training and awareness programs can bolster the understanding and implementation of security measures, reducing the risk of human error that could compromise transmitted data. Ultimately, a proactive approach to secure API data transmission strategies ensures enterprises maintain the trust of their stakeholders and comply with regulatory requirements, fostering an environment of reliability and data integrity.
Considerations for Secure API Data Transmission Strategies
Ensuring the security of API data transmission is a multifaceted endeavor that requires strategic considerations in its implementation. Organizations must evaluate their existing infrastructure to identify potential vulnerabilities that could be exploited during data transfer. Additionally, the complexity of API ecosystems necessitates a careful assessment of third-party systems and services involved in data exchange. Organizations must ensure that all integrated components employ secure communication protocols and adhere to established security standards.
Resource allocation is another significant consideration in implementing secure API data transmission strategies. Organizations must invest in state-of-the-art security technologies and employ skilled personnel to oversee the deployment and maintenance of these strategies. Continuous monitoring and assessment of API security posture are vital to identifying and mitigating emerging threats promptly. By dedicating adequate resources, organizations can ensure the robustness and reliability of their security measures, safeguarding the integrity and confidentiality of transmitted data.
Conclusion: The Future of Secure API Data Transmission Strategies
As the digital landscape continues to evolve, the importance of secure API data transmission strategies is set to increase. Organizations must stay agile and responsive to the changing threat landscape, adopting innovative security solutions that address emerging challenges. Furthermore, collaboration between industry stakeholders, regulatory bodies, and cybersecurity experts is paramount to developing effective security frameworks that align with evolving technologies and compliance requirements.
Secure API data transmission strategies serve as the bedrock of trust and reliability in the modern digital ecosystem. By implementing robust security measures and fostering a culture of security awareness, organizations can protect their data assets and maintain the confidence of their customers and partners. Ultimately, the effective implementation of secure API data transmission strategies enhances the resilience and credibility of organizations in an increasingly interconnected world.