In the contemporary landscape of rapidly advancing technology, secure digital communication protocols have become indispensable. These protocols play a pivotal role in ensuring the confidentiality, integrity, and authenticity of data transmitted across networks. With the exponential growth of data exchange activities, the necessity for robust security measures is more crucial than ever. Secure digital communication protocols encompass a wide array of technologies employed to protect information in transit, safeguarding it from interception, tampering, and unauthorized access. In this article, we delve into various aspects of these protocols, exploring their significance, mechanisms, benefits, and challenges in today’s digital age.
Read Now : Impact Of Artificial Intelligence Technology
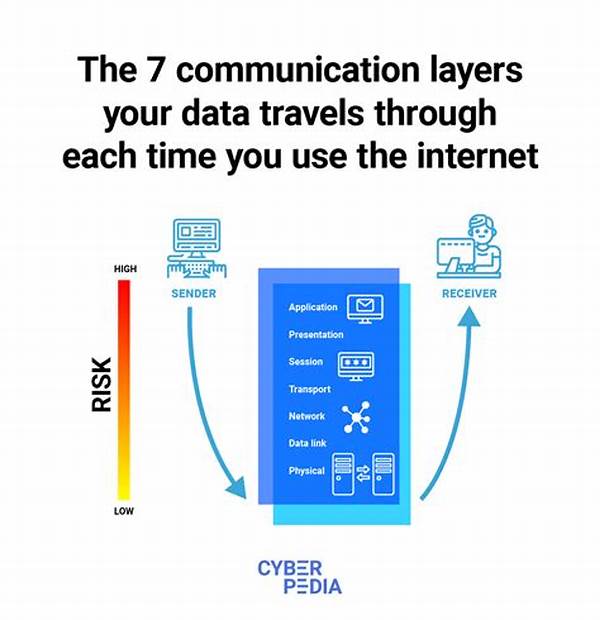
Understanding Secure Communication
Secure digital communication protocols are foundational components of modern information technology systems. They serve as the backbone of secure data exchanges, protecting information from myriad cyber threats. By employing encryption methods and integrity checks, these protocols ensure that data remains confidential and unaltered during transmission. For stakeholders in business, government, or personal communications, the adoption of secure digital communication protocols is imperative to maintain trust and compliance with privacy regulations. The evolution of these protocols continues to adapt in response to emerging threats and technological advancements, reinforcing their critical role. With an increasing reliance on digital communications, understanding the intricacies and functionalities of these protocols is essential for safeguarding sensitive information.
Key Features of Secure Protocols
1. Encryption: Secure digital communication protocols utilize advanced encryption to ensure data confidentiality during transmission.
2. Authentication: These protocols implement authentication mechanisms to verify the identities of users and devices.
3. Integrity: Secure digital communication protocols ensure data integrity through checks that detect and prevent tampering.
4. Non-repudiation: They provide non-repudiation features, ensuring that parties cannot deny their involvement in a communication.
5. Scalability: Secure digital communication protocols are designed to be scalable, accommodating growth and varying network sizes.
The Evolution of Protocols
Over the years, secure digital communication protocols have undergone significant evolution to address the changing dynamics of cyber threats and digital communication demands. Initially, protocols focused primarily on encrypting data between two points, ensuring that a message sent was the same as the one received. However, with the advancement in hacking techniques, protocols now incorporate sophisticated features such as multi-layered security and dynamic threat detection capabilities. Today, protocols like TLS (Transport Layer Security) and IPsec (Internet Protocol Security) have become industry standards, promoting secure exchanges over networks. These standards not only ensure confidentiality but also aid in authenticating communicating parties, thereby fortifying overall security frameworks.
Challenges in Protocol Implementation
Overcoming Security Hurdles
1. Complex interdependencies between protocol components can lead to vulnerabilities.
2. Variations in cryptographic standards challenge universal adoption.
Read Now : Consumer Behavior In Circular Economy
3. Integration complexities with legacy systems pose additional risks.
4. Evolving cyber threats require continuous protocol updates.
5. Performance trade-offs between security measures and system efficiency.
Maintaining Protocol Efficacy
Prominent challenges in implementing secure digital communication protocols include ensuring compatibility across diverse platforms and network environments. The conflict between maintaining security standards and achieving seamless user experiences further complicates deployment. Additionally, the resource-intensive nature of constant protocol updates can strain organizational capacities. Consequently, businesses and institutions must strike a balance between rigorous security protocols and practical usability. Organizations juggle maintaining protocol efficacy without sacrificing system performance. Nonetheless, secure digital communication protocols are fundamental to protecting data integrity and privacy on a global scale. As technology evolves, so too must the strategies that underpin these vital security measures, necessitating continuous vigilance and strategic adaptations.
The Future of Secure Protocols
The future of secure digital communication protocols looks promising with continued advancements in technology and cybersecurity. As quantum computing emerges, it is anticipated to revolutionize encryption methods, rendering current protocols obsolete. Thus, the development of quantum-resistant protocols is already underway to prepare for potential threats. Furthermore, as the Internet of Things (IoT) expands, more devices will require secure digital communication protocols to ensure safe data exchanges. This expansion necessitates protocols that cater to the unique demands of IoT environments, such as minimal resource consumption and heightened device interoperability. In an era where privacy and data protection are paramount, these developments herald a new dawn for secure communications, ensuring that data remains protected and trust is preserved in digital interactions.
Current Trends in Protocol Design
Innovations Shaping Protocols
Recent advancements in secure digital communication protocols have focused on enhancing security measures without compromising speed and efficiency. Protocols are now being designed with built-in adaptive security layers that react to the real-time detection of threats. Cryptographic agility remains a key design factor, allowing protocols to switch algorithms seamlessly in response to cryptoanalysis challenges. Additionally, protocol designs are increasingly emphasizing automation, enabling the self-healing of systems post-attack. Furthermore, the integration of artificial intelligence in protocol design is poised to revolutionize future iterations by enhancing threat prediction and response mechanisms.
A New Era of Communication
The trajectory of secure digital communication protocols is defined by a confluence of technological innovation and rising security consciousness. As businesses, governments, and individuals continue to navigate an increasingly interconnected world, the demand for secure communication solutions grows louder. Consequently, the development and implementation of advanced protocols can be seen as a foundational element in ensuring a safe digital ecosystem. The integration of machine learning algorithms into protocol development charts a course towards more predictive and adaptive security measures. This adaptability ensures protocols remain resilient and scalable, thereby supporting the fluid exchange of data in a secure manner. As the digital landscape continues to morph, the strategic evolution of secure digital communication protocols becomes increasingly critical for maintaining the sanctity and privacy of global communications.