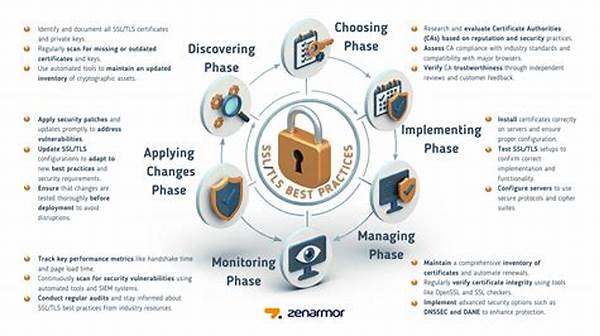
Ensuring the security and integrity of data transmitted over the internet is paramount, and SSL/TLS protocols play a vital role in this aspect. Proper configuration of these protocols ensures not only the protection of sensitive information but also maintains user trust. The process of SSL/TLS configuration best practices is both intricate and crucial for securing online communication. It involves selecting appropriate cipher suites, managing certificates securely, and keeping up-to-date with the latest security standards. This article explores best practices for configuring SSL/TLS to ensure robust security and optimal performance.
Read Now : Review Of Digital Education Applications
Importance of Proper SSL/TLS Configuration
The SSL/TLS configuration best practices are essential for safeguarding sensitive data and maintaining user confidence in web services. When SSL/TLS is configured correctly, it provides end-to-end encryption, preventing unauthorized parties from intercepting data. Poor configuration, on the other hand, can expose networks to vulnerabilities and exploits, undermining overall security efforts. The integration of these protocols with a strategic approach is imperative, given the sophistication of cyber threats. As digital communication becomes increasingly prevalent, the adoption of ssl/tls configuration best practices is non-negotiable. Organizations must continually update their security measures to protect against emerging threats, ensuring that they remain compliant with industry standards and regulations. In addition, implementing SSL/TLS correctly can facilitate better performance outcomes, including faster load times and improved search engine rankings, contributing to enhanced user experiences and reliability.
Configuring SSL/TLS involves several technical tasks which, if executed improperly, can lead to serious security lapses. Among the common missteps is the use of outdated protocols and weak cipher suites that are vulnerable to attacks. This underscores the necessity for organizations to remain vigilant and proactive, continually evaluating and updating their SSL/TLS configurations to conform with current ssl/tls configuration best practices. Regular security audits and assessments can provide insight into potential vulnerabilities, enabling IT teams to rectify issues expediently. Ultimately, the implementation of robust security protocols protects both organizational assets and client data, addressing privacy concerns in a digitally interconnected world.
Essential Components of SSL/TLS Configuration
1. Protocol Versioning: Utilizing the latest versions of SSL/TLS protocols is a key ssl/tls configuration best practice. This involves deprecating obsolete versions like SSLv3 and TLS 1.0, which are susceptible to various cyber threats.
2. Cipher Suite Selection: Opting for strong cipher suites is fundamental. The ssl/tls configuration best practices discourage the use of weak encryption methods that can be easily compromised, favoring robust alternatives that guarantee data integrity.
3. Certificate Management: Ensuring that SSL/TLS certificates are valid and issued by trusted Certificate Authorities is integral. This ssl/tls configuration best practice includes timely renewal and spatial monitoring of certificate expirations to prevent lapses in security.
4. Forward Secrecy: Incorporating forward secrecy into tls configurations protects session keys. This ssl/tls configuration best practice ensures past communications remain secure, even if long-term keys are compromised.
5. Secure Hashing Algorithms: Employing secure hashing algorithms like SHA-256 is recommended. As a part of ssl/tls configuration best practices, secure hashes mitigate risks associated with cryptographic breaks in weaker algorithms.
Implementing SSL/TLS Configuration Best Practices
To uphold the integrity of secure communications, organizations must adhere to ssl/tls configuration best practices by conducting routine audits and updates. By systematically scrutinizing configuration parameters, IT professionals can identify and mitigate weak points in global security frameworks. Appropriate staff training and awareness programs also form an essential component of effective SSL/TLS management. Education about evolving cyber threats and detailed operational guidelines empower personnel to implement and uphold ssl/tls configuration best practices efficiently, reducing the incidence of human error.
Investing in automation tools to manage ssl/tls configurations can further bolster organizational security. These tools streamline tasks such as certificate generation and renewal, cipher suite updates, and protocol version rollouts, all while adhering to industry standard ssl/tls configuration best practices. Organizations benefit from reduced administrative overhead, allowing for a shift in focus toward strategic security initiatives. With the rapid technological advancements, remaining agile and responsive to security needs is crucial, creating an environment where secure communications can thrive sustainably.
Read Now : “drought Impacts On Agricultural Output”
Consequences of Ignoring SSL/TLS Best Practices
Neglecting ssl/tls configuration best practices can lead to severe repercussions, affecting both technical infrastructure and public trust. The immediate consequence of neglect is heightened vulnerability to cyber-attacks, especially if policies are not in sync with current cryptographic standards. Breaches that exploit these weaknesses can result in unauthorized data access, potentially leading to significant data loss and reputational damage. Security incidents stemming from improper ssl/tls configurations often require extensive remediation efforts that drain valuable resources and disrupt business continuity.
Moreover, regulatory non-compliance is a potential risk when ssl/tls configuration best practices are ignored. Many industries are subject to strict data protection laws and failing to secure transmissions adequately could result in hefty penalties. Organizations may face a damaged reputation, diminished customer trust, and lost business opportunities, all of which underscore the critical importance of maintaining robust SSL/TLS configurations. Employing a proactive approach to compliance and adopting ssl/tls configuration best practices minimizes these risks, aligning security protocols with both legal requirements and customer expectations.
Strategic Insights on SSL/TLS Configuration
SSL/TLS configuration best practices are central to fostering resilient data protection mechanisms. Organizations striving to enhance their security postures must commit to continuous learning and adaptation. This involves regular training sessions for IT staff to hone their skills in SSL/TLS management, ensuring that they are equipped to handle the complexities of evolving security landscapes. It is also prudent for organizations to work with an array of security standards and practices tailored to their specific operational environments, embedding ssl/tls configuration best practices into their broader strategic frameworks.
Adopting an infrastructure that accommodates ssl/tls configuration best practices also focuses on fostering collaboration between different departments. Efforts to integrate business and security objectives serve as a foundation for more synchronized responses to potential security threats. By building a culture of security-centric decision-making, organizations not only protect data but also achieve long-term resilience. This approach acknowledges that security is a continuous journey rather than a one-time configuration, encouraging perpetual improvement and vigilance.
Conclusion and Future Directions
The implementation of ssl/tls configuration best practices signifies a foundational step towards impenetrable cybersecurity strategies. As organizations advance in their security efforts, the need for innovation in SSL/TLS management becomes apparent. Developing and leveraging cutting-edge technologies enables more sophisticated encryption techniques and intricate threat detection capabilities, which are integral to confronting future security challenges. Continuous investment in these areas fosters a robust security ecosystem, sustaining the protective measures essential to mitigating potential cyber threats effectively.
Furthermore, collaboration among industry peers and bolstering partnerships with trusted technology providers can facilitate the exchange of valuable insights and resources. These alliances can prove instrumental in navigating the complexities of ssl/tls configuration best practices, fostering environments conducive to active threat intelligence sharing. As cybersecurity continues to evolve, so too must the strategies and solutions employed. By approaching ssl/tls configuration with a proactive, informed perspective, organizations can navigate digital transformation confidently and secure their place as trusted custodians of data.